Remote Server Administration Tools (RSAT) are a core component of many IT professionals’ tool kits. However, the RSAT installation process changes with almost every new version of Windows. To clear up the confusion, here’s how to install RSAT on each version of Windows, including Windows 11, Windows 10, and — yes — even Windows 8.1.
What are RSAT tools?
RSAT tools enable sysadmins to manage Windows Server roles and features remotely. RSAT tools eliminate the need to log in to each of your servers to make changes. Instead, you can use RSAT tools to centrally manage your Windows servers.
The RSAT toolbox includes Group Policy management tools, Active Directory tools, DNS server tools, remote desktop services tools, SMTP server tools, Windows server roles management tools, and more. If you’re more of a scripter, you can rely on the Windows Terminal command line and Windows PowerShell cmdlets in the RSAT toolbox.
Note that you can run RSAT tools only on the Professional or Enterprise version of Microsoft Windows.
How to install RSAT on Windows 11
Windows 11 brought many changes to the world’s most popular desktop operating system, including how we install Remote Server Administration Tools. Here’s how to install RSAT tools on your Windows 11 PC.
Right-click on the Start icon, then click Settings.
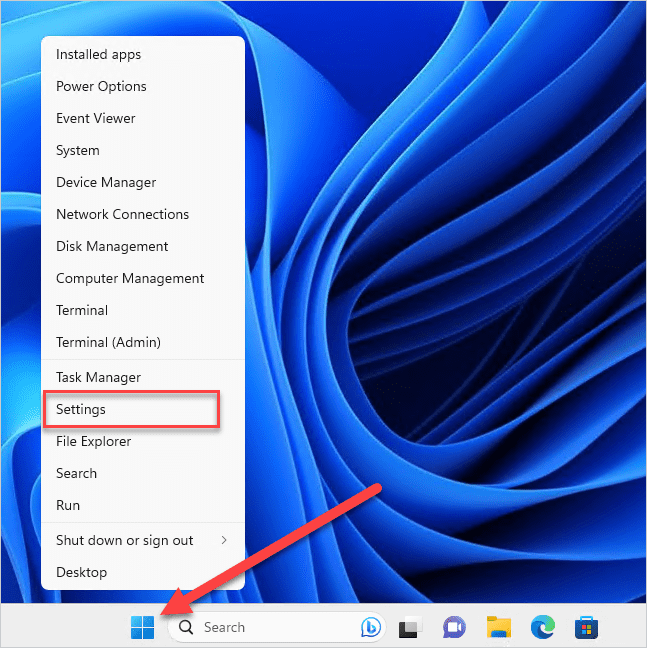
In the Settings menu, click Apps, then click Optional features.
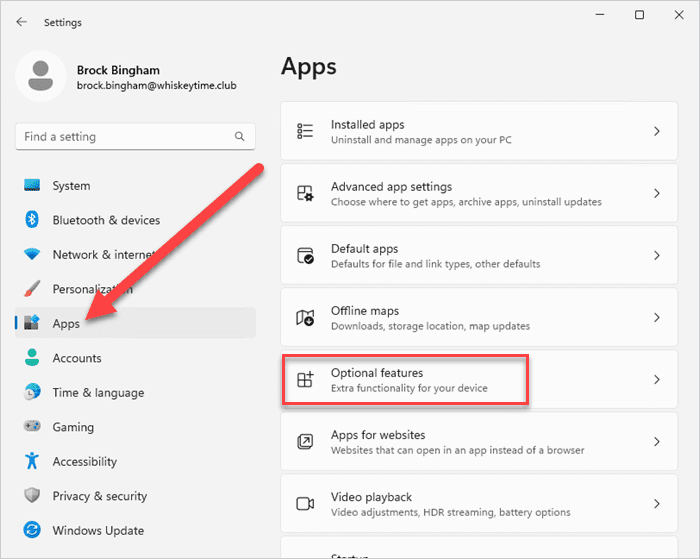
On the Optional features page, click View features.
Type RSAT into the search field.
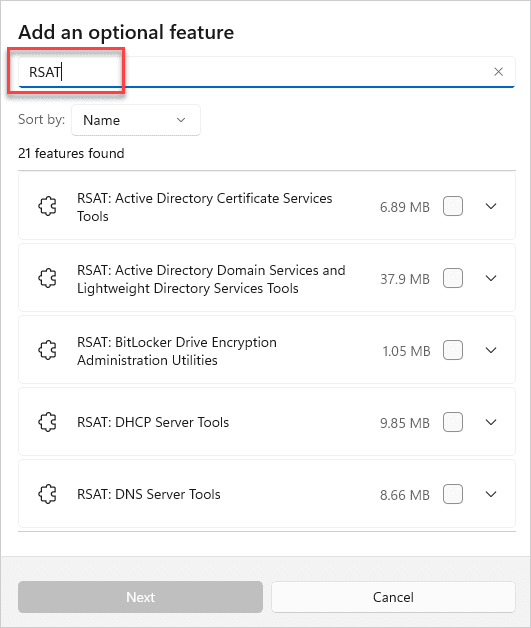
Select the RSAT features you want to install, then click Next.
Review the feature installation overview, then click Install.
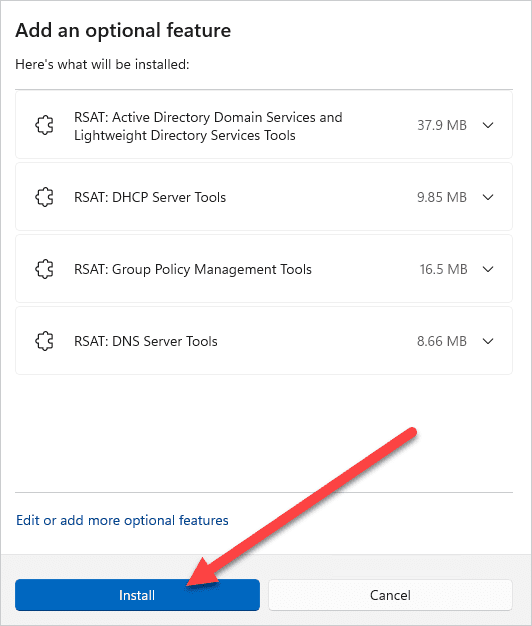
Monitor your RSAT install on the Optional features page.
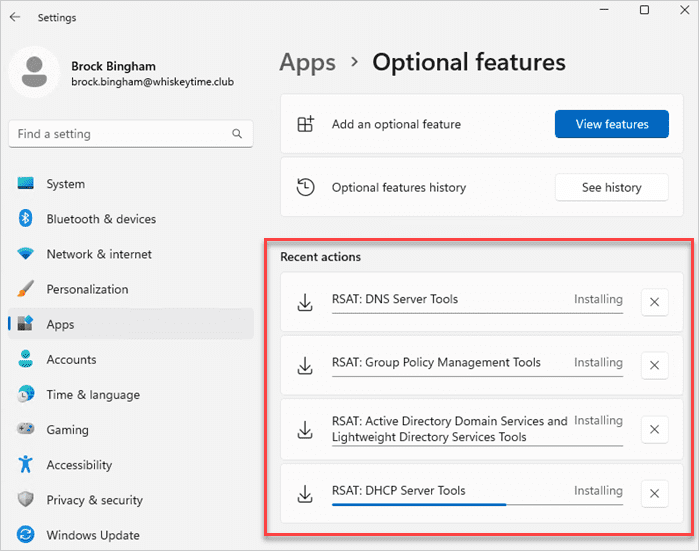
To find the RSAT features once installed, enter tools into the Windows search field, then click on Windows Tools.
How to install RSAT on Windows 10 (October 2018 update & newer)
If you're rocking one of the latest versions of Windows 10 (October 2018 update and newer), then you're in luck! As with Windows 11, the newer versions of Windows 10 come with Remote Server Administration Tools baked right into the OS. However, you still have to enable them.
Enabling RSAT features on Windows 10 is pretty similar to the Windows 11 process, with a few differences. Here's how to enable your favorite RSAT features in Windows 10.
Click the Start icon to open the Start menu.
Click the Settings icon to open the Settings menu.
Click Apps.
Click Optional features.
Click Add a feature.
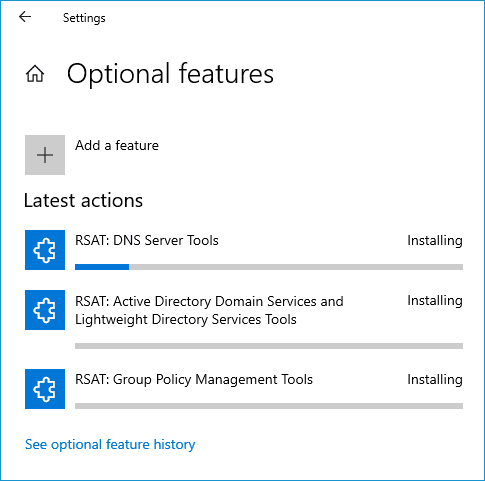
Scroll down the list of optional features until you find the RSAT features. Select whichever RSAT features you want to add, then click Install.
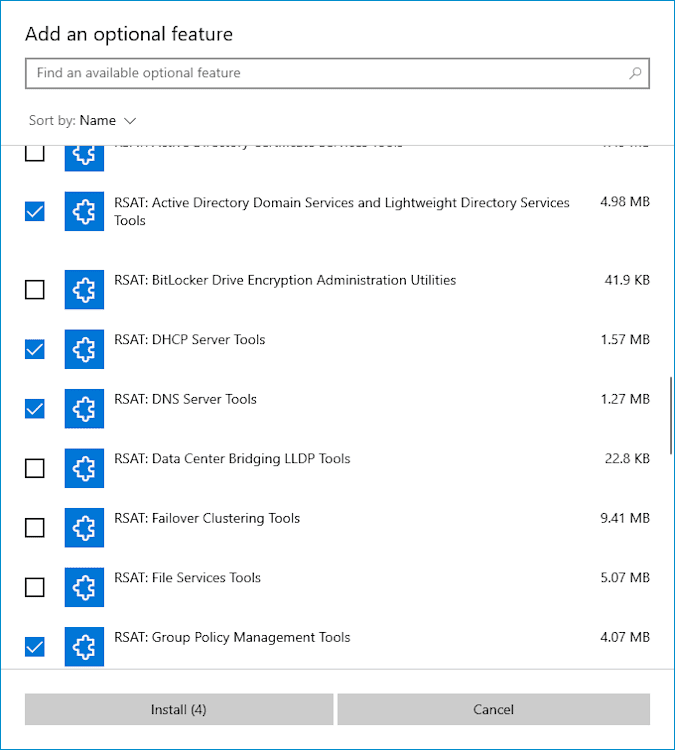
You will see the status of each RSAT feature that's being installed.
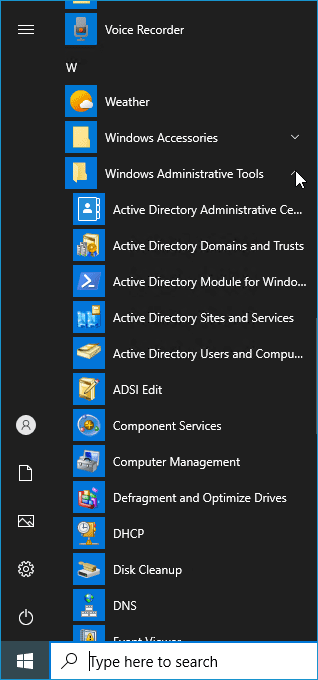
Once the tools have finished installing, you can access them through the Start menu in the Windows Administrative Tools folder.
How to install RSAT using Windows PowerShell
If you consider yourself a power user and love all things power — power tools, power steering, Powerade — then you might want a more powerful way to install Remote Server Administration Tools. If this sounds like you, here's how to install RSAT features using Windows PowerShell.
A quick note before we get started: To access RSAT via PowerShell, you need to run PowerShell as an administrator. To do that on Windows 10 or Windows 11, type powershell in the Windows search bar, right-click on the Windows PowerShell result, and click Run as administrator.
List all RSAT features and the installed state using PowerShell
First, we’ll use PowerShell to identify which RSAT features are currently installed. Here’s the script.
Get-WindowsCapability -Name RSAT* -Online | Select-Object -Property DisplayName, State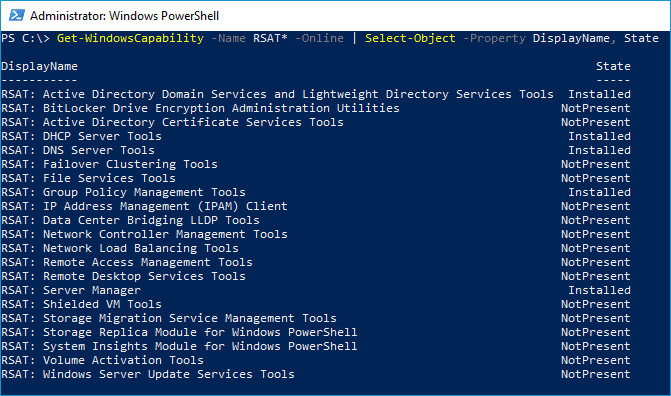
As you can see from this screenshot, this machine already has a few RSAT features installed.
Install a specific RSAT tool by name
Add-WindowsCapability -Online -Name "<tool_name>"Replace <tool_name> with the name of the Remote Server Administration Tool you want to install.
Here is a list of all the RSAT features with their proper PowerShell names.
For example, to install Remote Desktop Service Tools, run this command:
Add-WindowsCapability -Online -Name "Rsat.RemoteDesktop.Services.Tools~~~~0.0.1.0"How to install all RSAT features with one PowerShell command
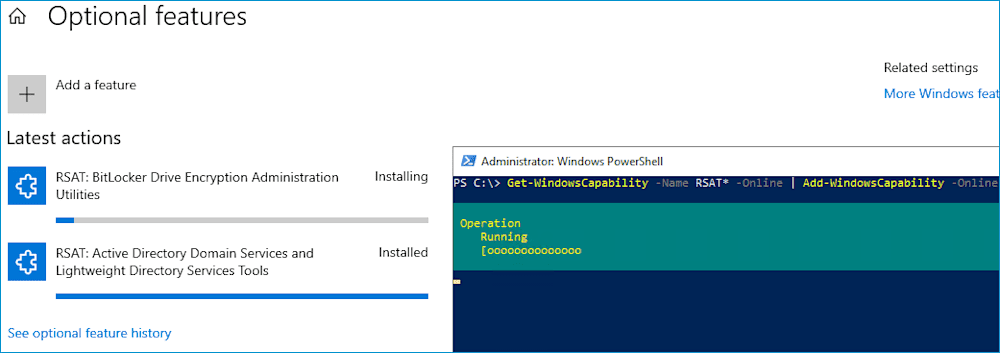
If you don't have the patience to install RSAT features one at a time, I don’t blame you. Instead, we can use this script to install all the available RSAT features in one go.
Get-WindowsCapability -Name RSAT* -Online | Add-WindowsCapability -OnlineIf you have the Optional features window open after running the command, you can monitor each feature as it's installed.
Easily run PowerShell scripts on remote devices
Need to run your awesome PowerShell scripts on remote devices? PDQ Connect can easily execute PowerShell scripts on any managed device with an active internet connection.
How to install RSAT on computers with older versions of Windows
In Microsoft’s perfect world, we’d all have the latest and greatest Windows PC, and we’d have zero complaints. (When pigs fly, am I right?) Instead, we live in a world with people like me who resist change while kicking and screaming. Thankfully, Microsoft still provides downloads for Remote Server Administration Tools for Windows 8.1 and older versions of Windows 10.
To install these RSAT packages, download the appropriate version for your OS, run the installer, and that's it. All features are enabled by default.
If you want to turn off certain features, you can select individual tools to disable by going into Control Panel > Programs > Turn Windows features on or off. In the Windows Features dialog box, expand Remote Server Administration Tools, and then expand either Role Administration Tools or Feature Administration Tools. Clear the checkboxes for any tools that you want to turn off.
As a side note, if you’re still running Windows 8.1 (a slight upgrade from one of the worst Windows operating systems), just know that I’m silently judging you from across the internet.
Remote Server Administration Tools are a great way to avoid getting out of your comfy office chair to manage server roles. They’re also great at alleviating server usage congestion. If you've got a coworker who never fails to log in to the server just before taking a three-hour lunch break (thus locking you out of the server), RSAT may be the solution you're looking for.
That, or maybe try switching their keyboard to the DVORAK layout when they aren't looking. That should keep them busy for a little while so you can get logged in before they do.
If you're looking for other tools to enhance your work life, download a free trial of PDQ Deploy & Inventory, and sit back and relax while this dynamic duo keeps your network environment up to date with the latest applications and patches. If you manage remote devices, then try out PDQ Connect. Connect helps you manage those hard-to-reach remote devices as if they’re right in front of you.