Remote Desktop Protocol (RDP) is an essential tool that users and sysadmins worldwide rely on daily. It’s also been the host of many vulnerabilities over the years and is a notorious attack vector for bad actors when exposed to the internet. Needless to say, securing RDP should be on your near-term to-do list. Thankfully, this helpful guide should get you most of the way there. Whether you’re running Windows 10, Windows 11, or Windows Server, we’ve got you covered.
Don’t expose RDP to the internet
With so many people working from home, exposing RDP to the internet may be tempting. But I humbly ask, in the name of all that is secure, please don’t.
Exposing RDP to the internet is not advisable, even when thoroughly secured. An exposed RDP port is a tempting target for bad actors, who will try to exploit RDP vulnerabilities and brute force passwords to gain access to your critical infrastructure.
Use a virtual private network (VPN) with RDP
The most secure way for remote users to use RDP is with a VPN connection. VPN usage skyrocketed since the pandemic and the great work-from-home (WFH) migration. Thankfully, VPN clients have gotten much better over the years. Provided you have a stable internet connection, VPN offers a seamless and secure remote work experience by encrypting your network traffic and keeping it safe from prying eyes and nosy ISPs.
Need help getting your users to remember to connect to the VPN? Just teach them this catchy phrase I just made up. When in doubt, VPN out. Man, I should apply for a job at Hallmark (pats self on the back).
Require long and complex passwords for RDP
Passwords are the first line of defense for most systems these days, and RDP is no exception. A strong password ensures your credentials can’t easily be brute forced.
Most people should be familiar with password complexity. However, password complexity recommendations are changing constantly. As computing equipment gets more powerful, the time it takes to brute force (or essentially guess) a password goes down. When I started in IT over a decade ago, the password complexity recommendations were eight characters of mixed-case characters, numbers, and symbols. Here are the current password complexity recommendations from CISA.
At least 16 characters long. The longer the better.
A mix of uppercase, lowercase, numbers, and symbols.
Don’t reuse passwords across accounts and services.
If you’ve dealt with enough users who’ve forgotten their passwords, you’ll know that 16 characters is a big ask. However, passphrases (a mix of multiple words) can be an easy way to make a password complex and still easy to remember.
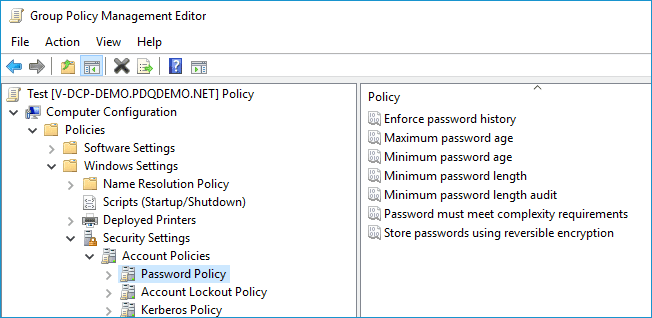
You can configure the Password Policy on your domain through Group Policy. The setting is located in Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Password Policy.
Limit login attempts
Limiting the number of login attempts before locking out an account is another way to deter brute force attacks. Brute force attacks can attempt thousands of passwords in seconds. However, if an account is locked out after three failed attempts, then the brute force attack stops in its tracks.
While this may sound like the perfect solution to brute force attacks, it does have drawbacks. If an attacker had access to usernames and wanted to, they could lock out hundreds or thousands of users from their accounts in a matter of seconds. Attackers could also use this method to harvest usernames because only valid usernames would become locked out of a system.
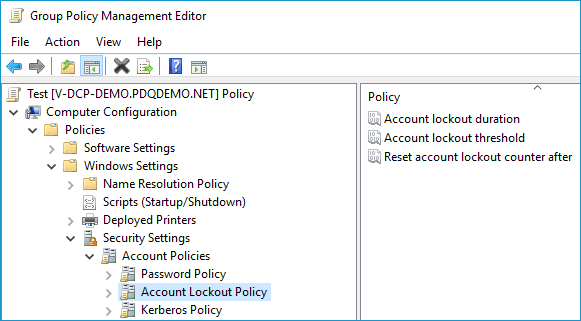
You can configure the Account Lockout Policy on your domain through Group Policy. The setting is located in Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Account Lockout Policy.
Update your systems to keep RDP secure
The advantage of RDP being a Microsoft-owned solution is the constant stream of updates. Microsoft is swift to patch vulnerabilities. Make sure you stay vigilant in keeping your systems patched and up to date. Just remember to review updates before applying them. Microsoft has been known to push updates that can break features or introduce new bugs.
Enable multifactor authentication (MFA)
Systems that implement MFA (sometimes referred to as 2FA or two-factor authentication) require users to provide multiple forms of authentication before granting access to a privileged resource.
MFA is highly regarded as an effective method of securing resources, including RDP connections. While phishing scams and brute force attacks have proven to be effective for obtaining user credentials, attackers will still be unable to access user accounts without the second form of authentication.
The most common downside to MFA is the added complexity for users when authenticating. However, MFA is common enough now that most users are accustomed to the process.
There are many more options for MFA today than there were even 10 years ago. Some possibilities include phone authentication, SMS and email token authentication, software token authentication, biometric verification, etc. With solutions provided by both Microsoft and third parties, you can find an MFA solution that works for your organization and helps secure your RDP sessions.
Reduce your attack surface in a few clicks
Looking for more ways to improve your security posture? Try PDQ Connect, and remediate vulnerabilities in seconds.
Use the principle of least privilege to secure RDP
The principle of least privilege is an ideology that directs organizations to limit user access to only necessary resources to perform their duties. If John Doe only needs access to Microsoft Office and a printer to do their job, they should only have access to Microsoft Office and a printer.
That means if most of your users don’t need to access network resources remotely, then they shouldn’t have access to RDP. This advice may be a given, but employees often change roles within an organization. It’s not uncommon for a user to change job responsibilities and maintain their existing network access. Your IT team should conduct regular audits to ensure you limit RDP access to those who require it.
Restrict local administrators from using RDP
By default, local administrator accounts have RDP access on non-domain joined computers. Using local administrator accounts to access devices remotely limits the effectiveness of logs used to identify users.
This situation worsens if an organization uses the same local administrator password on all its devices instead of using a solution like LAPS. Any user or attacker who obtains a local administrator password can now access any machine on the network. To mitigate this problem, restrict local administrators from using remote desktop. This restriction can be configured in the local security policy or through Group Policy.
Use non-administrator accounts
Whenever possible, users should log in to hosts using non-privileged accounts. This recommendation applies both when working on devices remotely and locally. By logging into workstations and servers with standard user accounts, you limit the risk of compromising privileged or administrator credentials. When a task requires administrative access, elevate privileges using the administrator credentials for that particular task.
Increase RDP security settings
Several settings can be configured through Group Policy to increase the security of remote desktop. With Group Policy open, you can locate these settings by going to Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services, Remote Desktop Session Host > Security.
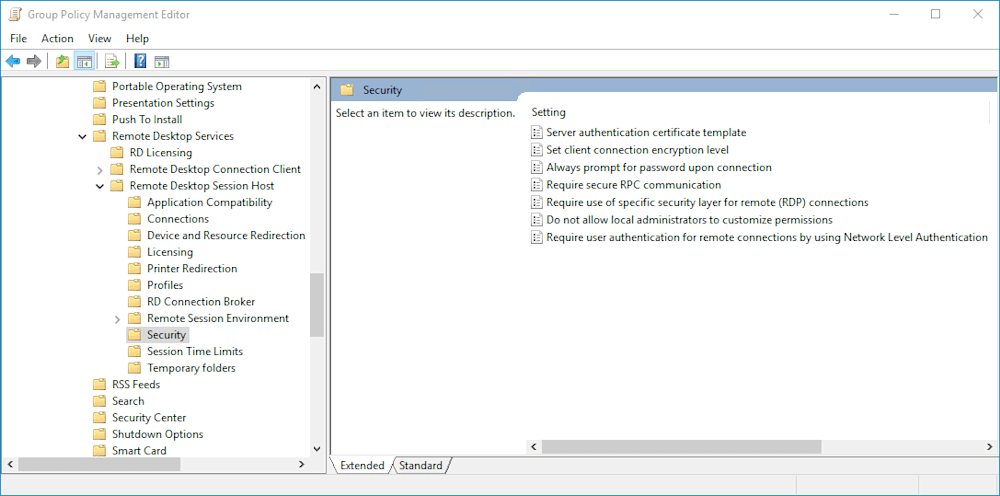
Review these settings to determine which would most benefit your organization. Here are a few recommended settings:
Set client connection encryption level: Enabled and set to High Level (if you have a mixed environment with older operating systems, you may want to set this to Client Compatible)
Require secure RPC communication: Enabled
Require use of specific security layer for remote (RDP) connections: Enabled and set to SSL security layer
Require user authentication for remote connections by using Network Level authentication: Enabled
Disable RDP if not in use
If you’re not actively using RDP, disable it. This advice goes for Windows 10, Windows 11, and Windows Server OS. If you have no intention to use a feature, disable it. Keeping unused features enabled broadens your attack vector and weakens your security posture.
Remote Desktop Protocol FAQs
What is Remote Desktop Protocol?
Remote Desktop Protocol (RDP) is a Microsoft technology that allows users to operate a remote computer over a network connection. It’s as if you were sitting directly in front of the remote computer. Keystrokes and mouse inputs are transmitted to the remote computer while the remote interface is displayed on the local device. Data is encrypted by RDP and transmitted over TCP/IP and UDP.
Does security through obscurity work for RDP?
Some individuals recommend changing the default RDP port to enhance security. While I love the phrase “security through obscurity,” obscurity — or changing the port number in this case — doesn’t provide enough protection to be worthwhile. A port scanner can quickly identify your RDP port, in which case, you’ve given yourself more work and only made yourself slightly more secure. There is nothing wrong with implementing this change. It just doesn’t provide any real security.
What’s the difference between RDP and remote desktop software?
There is some confusion about the differences between RDP and dedicated remote desktop software. Both are often referred to as “remote desktop.” However, while the two have many technical differences, the main difference is that RDP and dedicated remote desktop (or remote access) software function very differently and serve two different purposes.
RDP is intended to allow users to work on a remote device as if they were locally there, whether that’s a Windows 10, Windows 11, or Windows Server device. With RDP, you are the sole user operating your session on the remote device. Two users cannot share an RDP session, though multiple RDP sessions (each unique) can exist on Windows Server if configured properly.
Remote desktop, or remote access software, allows you to access another user’s device remotely. Sysadmins often use this to provide user support on remote devices, but it is not often used to work directly from a remote resource. Remote desktop software functionality differs from one solution to another, but most allow you to control the mouse and keyboard of the remote device, transfer files, and perform other administrative functions.
Remote desktop is a valuable tool for both users and sysadmins. It’s also been the source of many cyberattacks, which have cost organizations millions of dollars. Ensuring RDP is secure and properly configured is essential to network security.
Are you interested in other tools that can help you secure your IT assets? PDQ has you covered. Check out PDQ Connect, inventory your software and flag vulnerabilities that you can patch in just one click. And should something go wrong with a patch (which would totally not be Microsoft’s fault, of course), use PDQ Connect’s built-in remote desktop control and access feature to get things back up and running again.



