Recent Windows Local Administrator Password Solution (Windows LAPS) updates enhanced security. Unfortunately, they also affected how the platform works with PDQ Deploy & Inventory. Learn about what LAPS is, why it stopped working with PDQ Deploy & Inventory, and how to get the new LAPS up and running in Deploy & Inventory.
If you have gone through the pain of setting up LAPS only to find out that a Windows update wiped away all your hard work, this article is for you! Or if not, you know that you should limit the use of a Domain Admin account and instead use service accounts, preferably local accounts, to do your bidding. That's where LAPS comes into play. It’s a nice little solution that solves your security problem while still letting you get your work done. But there's one little problem: It had a big fight with Deploy and Inventory. (They were on a break!)
What is LAPS, and is it really new?
Windows LAPS is an established solution for managing local administrative passwords on Windows Server Active Directory-connected devices. It automatically handles and secures these passwords, storing them in Active Directory and Azure Active Directory with encryption. You can control access to the password based on permissions.
You might have come across the older Microsoft endpoint security tool, also known as legacy LAPS, which was available for some time on the Microsoft Download Center. It functions by regularly changing the password and maintaining a backup in Active Directory (AD) or Azure AD. In our discussions, we'll refer to this older product as "legacy LAPS." (Kind of like me. I’m not old — I’m vintage.)
Legacy Microsoft LAPS requires an MSI package deployment on each target device to function effectively. This was a pain! In contrast, the newer iteration of LAPS streamlines the process by integrating seamlessly into Active Directory without the need for individual MSI installations on devices. This improvement simplifies deployment and management, making the newer LAPS solution even more efficient and user-friendly.
Why did LAPS stop working with PDQ Deploy & Inventory?
In April 2023, LAPS underwent a significant transformation, catching Deploy & Inventory tools by surprise. Previously, LAPS stored the admin password openly in the AD attribute editor, devoid of encryption. Deploy & Inventory knew precisely where to look. However, the April 2023 update changed the game. Microsoft, in its customary fashion, revamped things. Shocker, right? I’m convinced there are entire departments dedicated to moving things around.
The new LAPS became more sophisticated and security focused — a positive step. Yet, as with any major Microsoft update, it introduced some disruptions. That is Microsoft speak for “this update is going to break a bunch of stuff, and our help documentation is going to be of absolutely no help at all.” Oh goodie! I get to waste a bunch of time reading 10 articles that vaguely tiptoe around the issue but don’t tell me how to fix it. Time to go to Reddit and find some other rabid sysadmins facing the same issue who actually have a solution. Grrrr! I’m suddenly blinded by rage. What were we talking about? Oh yes, new LAPS.
The AD schema expanded in the new Microsoft LAPS, birthing a fresh tab on the AD object, aptly named LAPS. Here, LAPS now securely keeps its admin name and, just for funsies, encrypts the password, taking on a secret-agent vibe. This relocation left Deploy & Inventory tools searching in vain at the old address within the attribute editor. The absence of a forwarding address perplexed them, severing the connection with LAPS. It was an unfortunate chain of events driven by LAPS's added security layer. While fixable, once Deploy & Inventory tools locate the new address, they'll know where to find LAPS and its keys.
Prereqs for new LAPS
Here are the basics for the new version of LAPS. You need to be running either Windows 10 or 11 H2s on your machine. For the server folks, Windows Server 2019 or 2022 is where it's at. Don't forget to run the April 2023 update on your domain controller. You won’t get anywhere unless you do this step. No. Seriously. Run this update.
Time for the PowerShell
Next, it's time to run a few PowerShell commands on your domain controller (DC). This is a little different than legacy LAPS. Remember — we are adding an additional tab to AD, so we need to run additional steps.
Let’s run PowerShell — as Administrator, of course. Is there any other way?
Start with:
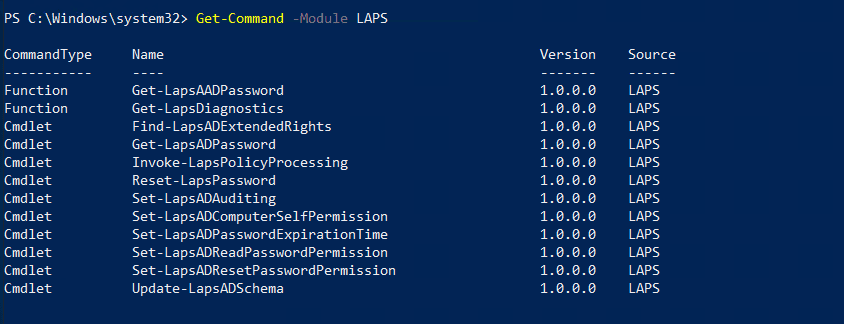
Get –Command –Module LAPS
Get –Command –Module LAPSThis verifies that the LAPS module is loaded.
Run the following parameter:
Update-LapsADSchema -Verbose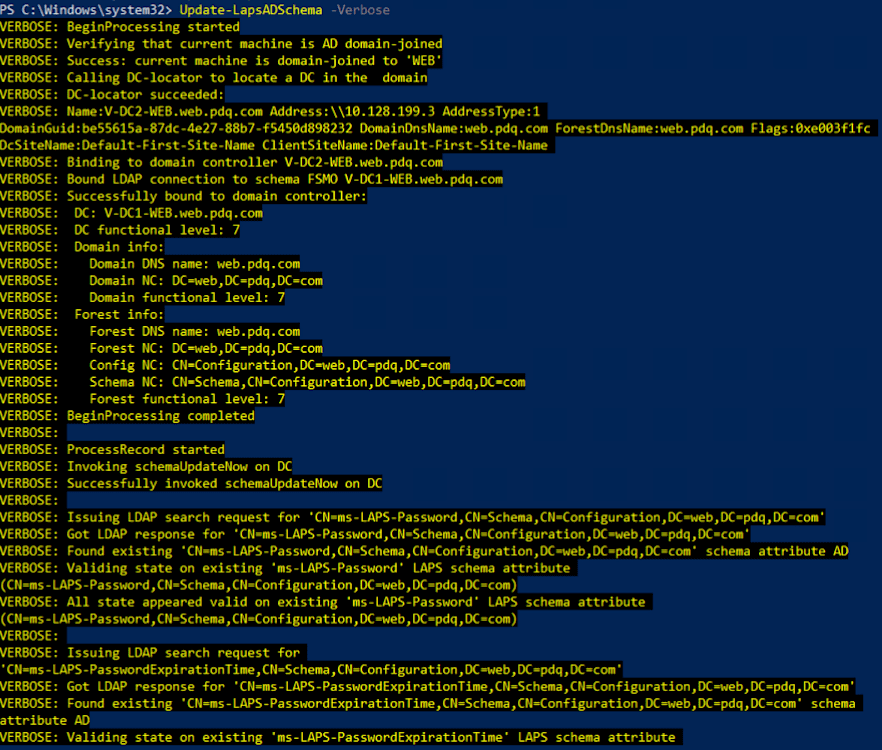
Configure security on an Active Directory (AD) organizational unit (OU) to grant specific users or groups permission to query Windows Local Administrator Password Solution (LAPS) passwords.
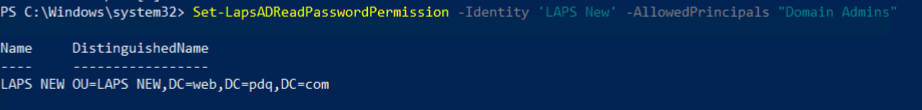
help Set-LapsADReadPasswordPermission -Online Group Policy
Now it’s time to tackle Group Policy. Let’s open the Group Policy Management Console. We need to get rid of your old LAPS Group Policy Object (GPO). Make sure you unscope it and give it at least 3 days to refresh. In the meantime, you need to create a new local admin on the machines. Some people say you don’t need to do this, but I did. So, why not just do it? Although there are PS scripts to add a local admin and various other methods, they all have some security risks. I would suggest using GPO to do this part. It’s not fancy, but it works, and it’s secure.
Once you have done the above step, it's time to make the LAPS GPO. You might need to update your .ADMX templates on your domain controller. I’m sorry; it’s an MS guide. Sigh. This part was a pain! Even though I ran the update, I needed to manually update my templates. So annoying! Where is SYSVOL again?! Gah! Why wouldn’t I have replication issues with my domain controllers? Stupid computers! After some expletive-filled rants, I managed to update my templates and was ready to make my new GPO.
Determine if you have new .ADMX templates
If you pay attention to nothing else, listen to this! Here is how you know you have the new templates:
The legacy LAPS GPO and the new LAPS
Legacy LAPS used to live here:
Computer config > Policies > Admin templates > LAPS.New LAPS lives here:
Computer config > Policies > Admin templates > System > LAPS.
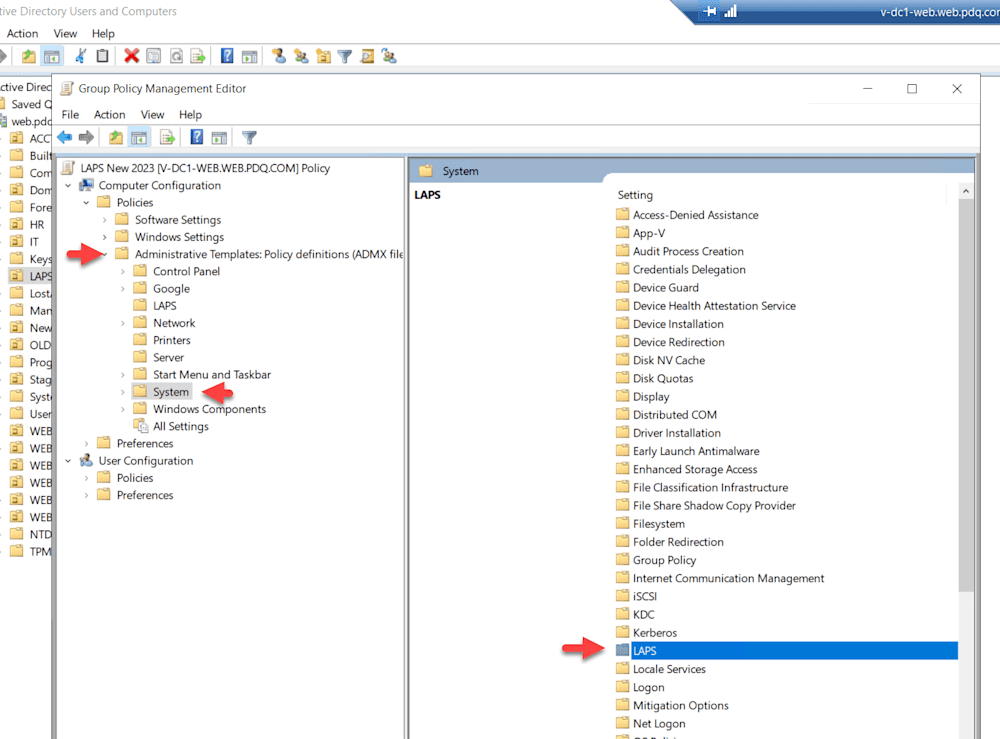
As we expand the policy, we can see all the settings we changed.
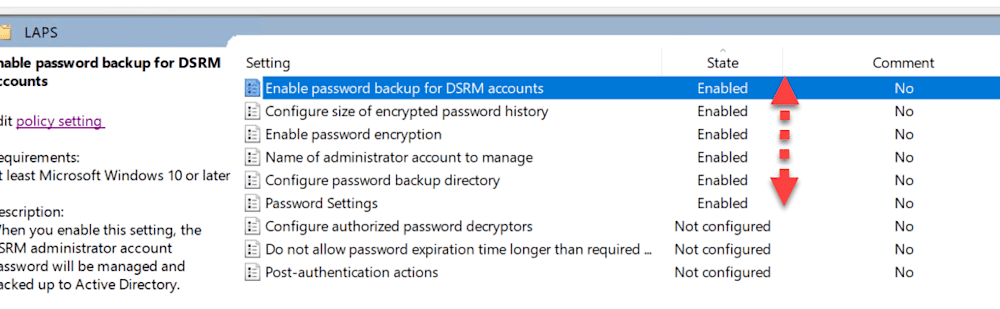
First, we need to create an admin account. Come on, Barbie, let’s go party! (I may or may not have just seen the Barbie movie.) Make sure this matches the name of the new admin account you just created.
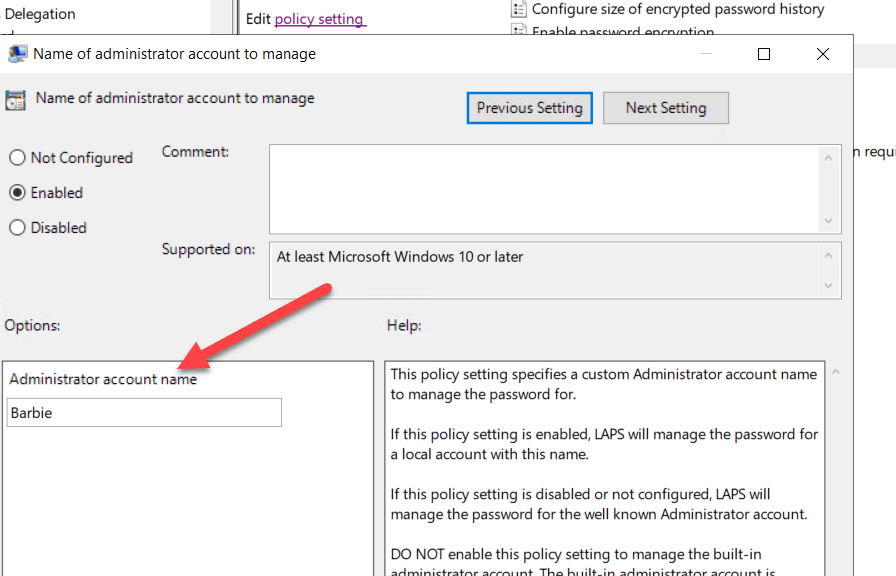
Next, we are going to pick the backup directory. Since Deploy & Inventory only work with Active Directory, you need to specify AD here.
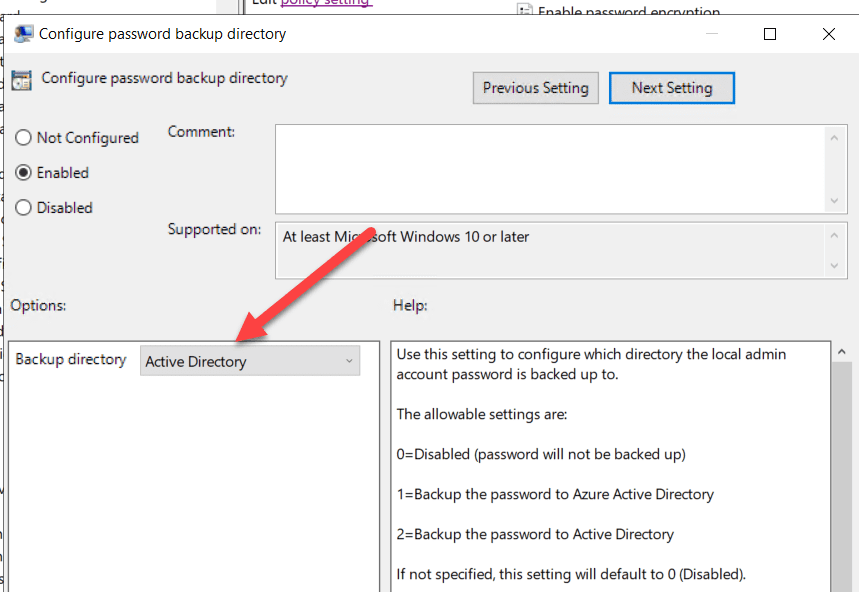
This next part is where we configure the password complexity and age. Set this according to your environment’s security specifications.
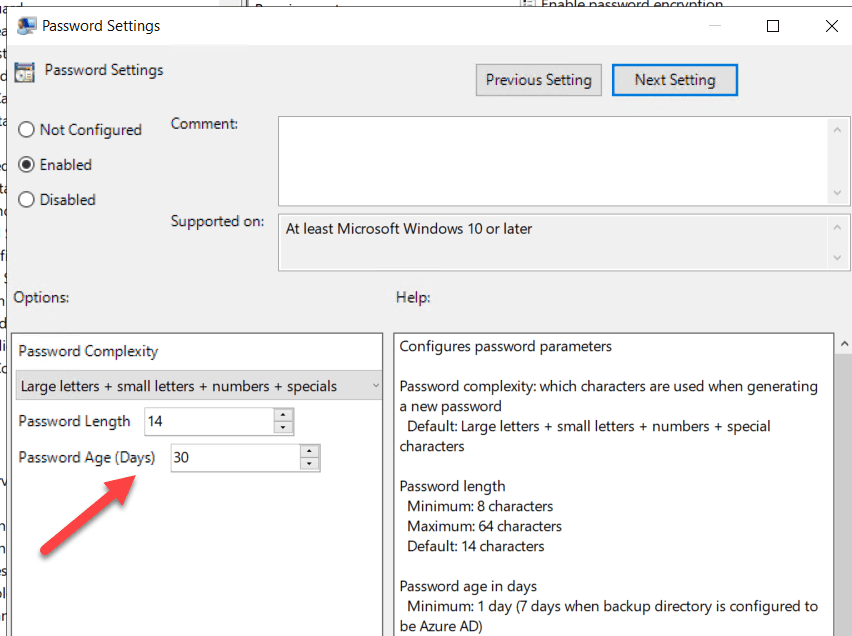
Save your GPO and scope it accordingly. Full disclosure: This did take some time to trigger. I may or may not have compulsively run gpupdate /force over and over again to no avail. It took 24 hours before it worked. Here is how you know it works. You will see this in Active Directory:
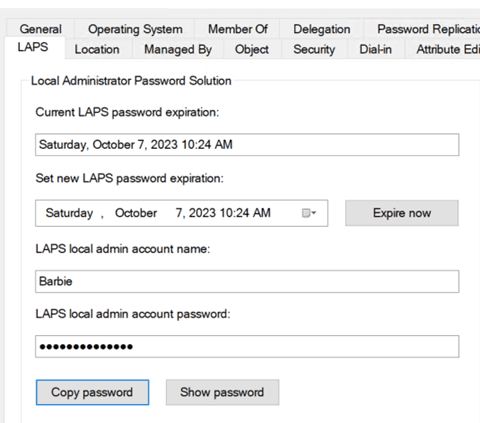
All of these fields in AD will be populated. Success!
Open Deploy & Inventory
Now that we have done all the prep work, we are good to go. The good news is, if you have already done the setup work in Deploy & Inventory, LAPS will work again. Take your new local admin account and follow this LAPS integration guide to get your new credentials up and running.
You may — and when I say may, I mean you will — run into an access denied error; you will need to turn off remote UAC. I know, I know. Your security peeps are not gonna be happy. But think of it this way: You are trading one security feature for another. Pick your poison, people! By its very nature, LAPS does not allow any program to run local credentials from a remote machine. So we are gonna blame Microsoft for this one.
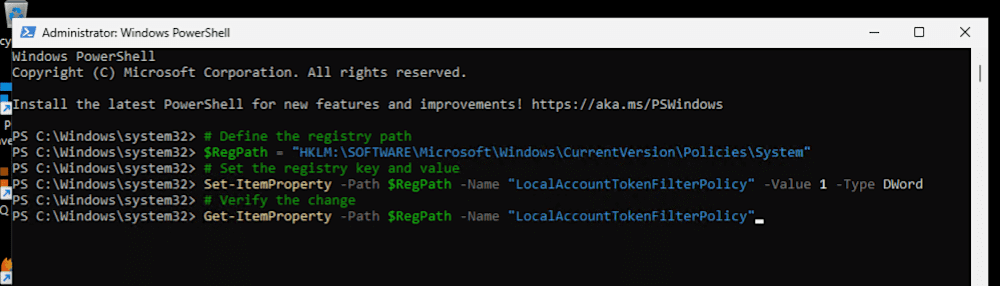
You can turn off remote UAC via GPO, or you can use this handy PS command in Deploy & Inventory. The choice is yours.
LAPS also works with Microsoft Intune using configuration policies, the GPOs of the cloud. You can use these, along with conditional access policies, for a greater level of security for your devices. Unfortunately, Deploy & Inventory do not integrate with Azure AD (or Microsoft Entra, or whatever they are calling it this week), so they're dead to us.
Since I know you're like me and you like to keep things tidy, the very last thing you need to do is uninstall the MSI from legacy LAPS. Lucky for you, I’m including an uninstall guide using Deploy & Inventory so you can do it quickly and easily. If you aren’t already using Deploy & Inventory, why not sign up for a free trial today?
Loading...