When everything’s on fire — sometimes literally — your disaster recovery plan is the only thing standing between chaos and continuity. A solid DRP isn’t just a compliance checkbox; it’s the difference between a bad day and a business-ending outage. Whether you’re defending against ransomware, hardware failure, or someone deleting the wrong S3 bucket, this disaster recovery plan template helps your IT team react fast while staying organized and minimizing downtime.
How to prepare a disaster recovery plan: Checklist
Before you start filling out your DRP, it’s worth making sure your foundation isn’t built on wishful thinking. This checklist helps you take stock of what you actually have, what really matters, and what will hit the fan first.
☐ Inventory your assets
List all hardware, software, data, and cloud services in use. Remove redundancies to simplify backup and recovery.
☐ Identify critical resources
Prioritize systems essential to business operations so you know what to recover first.
☐ Clarify recovery objectives
Define your KPIs, like recovery time objective (RTO) and recovery point objective (RPO) for each critical system. These numbers will shape the rest of your plan.
☐ Assess risks and threats
Perform a business impact analysis and identify likely disaster types (e.g., natural disasters, cyberattacks, outages, human error).
☐ Establish a data backup plan
Decide where and how you’ll store backups (cloud, offline, hybrid), how frequently, and how you’ll validate them.
☐ Determine key team members
Assign roles for incident response, recovery, communications, and testing — plus backups for each.
☐ Create a communications plan
Specify who to contact, how to reach them, and how to notify internal/external stakeholders.
☐ Document your network infrastructure
Maintain an up-to-date map of assets, dependencies, and access paths for recovery.
Core DRP framework
Now that you’ve got the groundwork handled, this section turns your checklist into an actionable plan. These prompts walk you through every part of a complete disaster recovery plan — from executive summary to postmortem review.
1. Executive summary
Start with a quick snapshot of your disaster recovery plan, including what it’s for, what it covers, and why it matters.
Fill in:
☐ What is the primary objective of the plan?
Ex. Ensure customer-facing applications are restored within 4 hours to minimize business disruption and SLA violations.
☐ What types of disasters are covered (natural, cyber, operational)?
Ex. Cyberattacks (e.g., ransomware), cloud infrastructure outages, accidental data loss, regional natural disasters.
☐ What business risks or losses are you trying to prevent?
Ex. Loss of revenue, SLA breaches, customer churn, reputational damage, regulatory fines.
2. Scope of the plan
Make it clear where this plan applies and where it doesn’t so that there’s no confusion when a crisis hits.
Fill in:
☐ Which systems, teams, or types of data are covered?
Ex. All production systems hosting customer data; excludes dev/test environments.
☐ Are any departments, locations, or tools excluded?
Ex. Internal HR and finance tools are not covered under this DRP.
☐ Will you need separate plans for different kinds of disasters?
Ex. Yes — separate plans exist for cyber incidents (e.g., ransomware playbook), natural disasters (facility-specific evacuation + remote access plan), and cloud outages (failover procedures in AWS runbook).
3. Roles & responsibilities
List out your disaster recovery team so everyone knows their job when it’s go-time. And don’t forget backups (for the people, not just the systems).
Fill in:
☐ DRP owner:
☐ Backup lead(s):
☐ Communication lead:
☐ System-specific contacts (e.g., Active Directory, SQL Server):
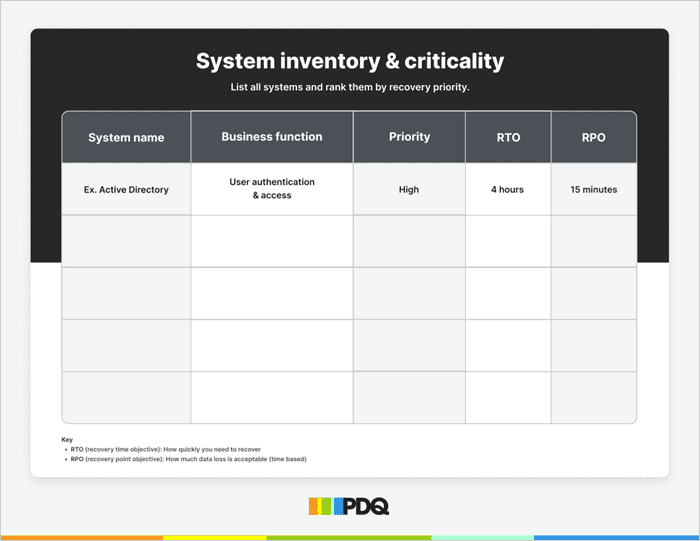
4. System inventory & criticality
List all systems and rank them by recovery priority.
RTO (recovery time objective): How quickly you need to recover
RPO (recovery point objective): How much data loss is acceptable (time based)
5. Backup & recovery procedures
Describe how you’ll recover systems and data.
Fill in:
☐ Frequency and location of backups (daily, offsite/cloud, immutable)
Ex. Daily backups stored in AWS S3 (versioned), plus weekly offline snapshot to encrypted external drive.
☐ Manual vs. automated restoration processes
Ex. File restore is automated via Veeam; SQL database recovery requires manual log replay.
☐ Authentication and access control steps
Ex. MFA required to access backup portal; credentials stored in password vault with emergency access protocol.
☐ Known dependencies (DNS, SSO, integrations)
Ex. SSO service must be online before user logins work; recovery order: DNS → SSO → primary apps.
6. Communication plan
Explain how internal and external stakeholders will be notified.
Fill in:
☐ Who needs to be informed (execs, employees, customers)?
Ex. Executive team, employees via Slack + email, customers via status page and support mailing list, compliance team (if data breach suspected).
☐ Preferred channels (email, SMS, Slack, status page)
Ex. Internal comms via Slack and SMS; customers notified through status page and email.
☐ Who approves outbound messaging?
Ex. Director of IT for internal; Head of Comms for external.
☐ Offline communication alternatives
Ex. Printed emergency contact list for IT and executive team, backup phones with prepaid SIMs, prewritten SMS templates for mass notification.
7. Testing & maintenance schedule
Ensure the plan actually works.
Fill in:
☐ When was the plan last tested?
☐ Frequency of testing (quarterly, annually):
☐ Who runs the tests?
☐ What constitutes a successful test?
Ex. Recovery of all tier 1 systems within defined RTO/RPO, with audit logs reviewed and no security incidents.
8. Postmortem & continuous improvement
Have a plan for improving your plan.
Fill in:
☐ What’s your process for reviewing real-world incidents?
Ex. Schedule an RCA meeting within 72 hours of a DR event. Use a standard postmortem template.
☐ How do you update the plan after a DR event?
Ex. After-action items are assigned in Asana; DRP updated in Confluence with version control by the IT lead.
☐ Where is the updated DRP stored/shared?
Compliance & documentation checklist
Regulators love paperwork almost as much as sysadmins hate rework. Use this final checklist to make sure your plan is complete, compliant, and accessible.
☐ DRP document is version-controlled and stored securely
☐ DRP includes the date of last review and version number
☐ Backup and recovery logs are retained
☐ DRP complies with industry-specific requirements (e.g., HIPAA, ISO 27001, PCI-DSS, etc.)
☐ Multiple secure copies of the plan exist (cloud + physical)
☐ Team members have signed off on the current version
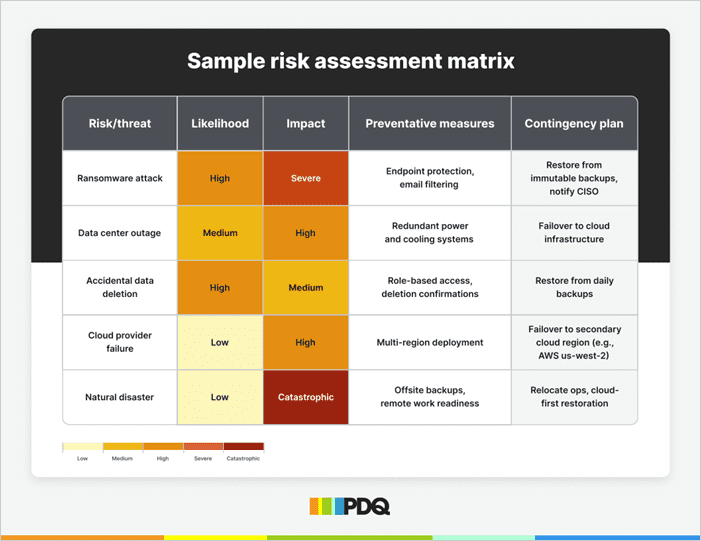
Sample risk assessment matrix
A risk assessment matrix helps you rank potential IT disasters by likelihood and impact so you can prioritize preventive actions.
Disasters are inevitable — downtime doesn’t have to be. A well-built disaster recovery plan keeps your organization resilient and your nights slightly less sleepless. And if you’re looking to make endpoint recovery less of a guessing game, snag a free trial of PDQ Connect and see how easy it is to keep every system visible, patched, and ready for whatever comes next.