Ransomware Attack Patch
Important Note: Due to the critical nature of the WannaCrypt ransomware attack, we have made the Windows Update patches temporarily available to Pro customers as well as Enterprise customers until May 31, 2017. After May 31 these patches will be exclusive to Enterprise customers.
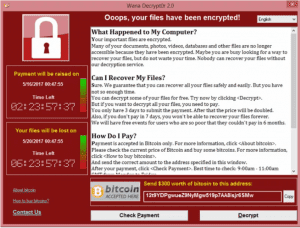
On Friday May 12, one of the largest ransomware attacks in history was detected in several European countries and has since spread to over 150 countries world-wide. The WannaCrypt (also called WannaCry) ransomware attack exploits a vulnerability in older versions of the Microsoft Windows operating system, encrypts your data, and holds that data hostage until a ransom is paid. There is, however, a ransomware attack patch available. PDQ Inventory will help you identify which computers need to be patched and PDQ Deploy can deploy the patches.
Identify Vulnerable Computers With PDQ Inventory
On March 14, Microsoft issued a security update to patch this operating system vulnerability. Use the collection created in the PDQ Inventory Collection Library to identify which computers on your network require the patch.
Deploy The Patch With PDQ Deploy
Once you have identified the computers that require the patch, use PDQ Deploy to deploy the patch and update your systems. The patches in the PDQ Deploy Collection Library installs the WannaCrypt patches for unsupported operating systems (XP, 2003x, 2008, Win8). Patches are also available for supported OS versions.
See how to manage this threat in this video:
Loading...
Important Link:
WannaCrypt Out Of Band Patches (Old OS) 1.0