Automated vulnerability patching identifies, prioritizes, and deploys security updates across systems without manual work. It shortens the security patching process, reduces missing patches, and minimizes human error. Here’s how to get started (and how PDQ Connect makes it absurdly easy).
How does automated vulnerability patching work?
Automated vulnerability patching uses a repeatable cycle of vulnerability detection, prioritization, and patch deployment. Here’s how the process typically works:
Scan systems for known vulnerabilities: Use security tools to detect missing patches or misconfigurations based on vulnerability databases.
Match vulnerabilities to available patches: Identify which software updates can resolve the detected issues.
Prioritize based on severity and exploitability: Use CVSS scores and threat intelligence to decide which patches to apply first based on severity and exploitability.
Deploy updates: Apply the relevant patches to affected systems using automated tools and workflows.
Think of it like a conveyor belt for patches: Once it's set up properly, it becomes efficient, controlled, and scalable (three of our favorite things, right after free snacks and uptime).
How to get started with automated vulnerability patching
Automated vulnerability patching reduces risk and saves time — but only if you roll it out smartly. Here’s a crawl-walk-run approach to launching automation without breaking stuff or losing sleep:
1. Audit your current patching process
Before you touch automation tools, map out how your environment currently handles patching. Identify:
How patches are tested and deployed
Which systems get patched regularly (and which don’t)
What tools (if any) are currently in place
This information gives you a solid baseline to spot gaps, avoid duplicate efforts, and see where automation can make the biggest impact.
2. Choose the right automation tool
Look for vulnerability patch management software that integrates well with your OS mix, security tools, and update cadence. Key features to prioritize:
OS and third-party patch support
Scheduling and reboot control
Reporting and rollback capabilities
For Windows-heavy shops, tools like PDQ Connect can be especially handy.
3. Set policies by system criticality
Not every machine needs the same patching urgency. Segment systems by risk and sensitivity:
High-risk (public-facing servers, endpoints): Patch ASAP
Medium-risk (internal tools): Patch regularly (biweekly or monthly)
Low-risk (lab machines, cold storage backups): Patch on a set schedule (quarterly or during routine maintenance windows)
This way, you reduce the attack surface without overloading your team.
4. Configure your automation settings
Now the fun begins. Start with basic automation:
Define patch scan intervals
Set auto-approval rules for known-safe updates
Establish reboot behavior (prompt, defer, or force)
Avoid setting everything to “auto” on day one. Instead, build confidence (and learn valuable lessons) with a controlled rollout.
5. Pilot in a low-risk group
Choose a test group — maybe a few dev laptops or a QA server cluster — and monitor results closely. Check for:
Successful installs and reboots
App compatibility issues
Gaps in patch reporting
This dry run helps validate your logic before you scale up. Break things gently and learn quickly.
6. Roll out gradually (with rollback plans)
Once your pilot looks good, expand in stages. Add one department or system group at a time. Keep rollback options ready (snapshots, uninstall scripts) in case a patch nukes a critical app.
How to maintain secure automated patching
Once patch automation is live, the next challenge is keeping it secure, stable, and trustworthy. These practices help you harden the system, catch issues early, and stay audit ready. Here’s how to do it right.
1. Establish a known-good baseline
Snapshot your environment (OS versions, apps, patch levels) so you can trace issues and roll back if needed.
2. Use ongoing ring-based deployment
Keep using a ring model post-rollout. Update pilot machines first, then proceed in waves to reduce blast radius if something goes wrong. Think toe in the water, not cannonball.
3. Schedule patches for low-impact hours
Time updates to avoid disrupting business. Overnight installs or deferred reboots minimize user complaints.
4. Log and audit everything
Centralize logging to make it easier to verify patch success, monitor for anomalies, and prep for audits.
5. Track failures and automate patching retries
Set up alerts for failed installs or skipped systems. Automate safe retries, or flag for manual review if systems show post-patch instability.
6. Retest your automation periodically
When you update your patch management tool or security baselines, rerun test deployments in your pilot group to ensure nothing is broken. When should you patch vulnerabilities manually? Automation is powerful, but sometimes you’ve gotta roll up your sleeves. Manual security vulnerability remediation may be better when:
No patch is available.
You're dealing with legacy systems or highly customized apps.
A patch has a track record of breaking stuff.
Root cause analysis needs human eyes.
Basically, if it’s fragile, weird, unknown, or haunted, get in there manually. Let automation handle the straightforward stuff so that you have the time for edge cases.
Common challenges with vulnerability patch automation
Automated vulnerability patching is helpful, but it isn't foolproof. IT teams may run into issues that automation can’t predict. To maintain secure, stable systems, you need to recognize potential pitfalls.
False positives in vulnerability scanner results: Some vulnerability scanners flag issues that aren’t exploitable or are already mitigated, leading to wasted effort or misplaced urgency.
Patch conflicts with custom configurations: Automated patches can break applications or scripts that rely on specific OS behaviors, registry keys, or older dependencies. This is especially risky in environments with homegrown apps, legacy tools, or nonstandard configurations.
Excessive patching that causes downtime: Over-patching without considering operational impact (e.g., reboot cycles, service restarts) can disrupt productivity.
Limited visibility on BYOD or offline endpoints: Devices outside of centralized management (BYOD, roaming laptops, field equipment) may miss patch cycles entirely or inaccurately report patch status. Automation solutions can't guarantee compliance on assets they don’t fully control.
Even the best automation can struggle with unique or misconfigured environments. A little oversight goes a long way.
How do you automate vulnerability patching with PDQ Connect?
PDQ Connect enables automated vulnerability patching for hundreds of popular third-party applications. If the app is in our built-in CVE detection and extensive Package Library, you can automate vulnerability patching for it. We’ll walk you through the process.
"You can literally patch a browser vulnerability in 30 seconds." — Zach Fegan, PDQ sales engineer lead — IT and InfoSec: Why it feels like a turf war (and how to fix that)
1. Click the Vulnerabilities tab. Highlight a CVE, and click the Automate button.
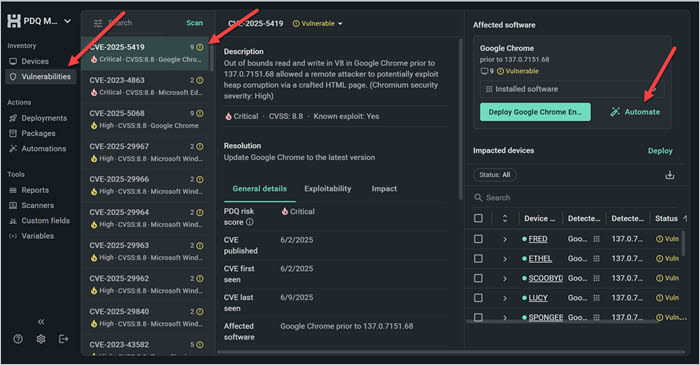
2. A new window opens with an automation designed to patch any version of the software with known vulnerabilities. Check the details, then click Confirm.
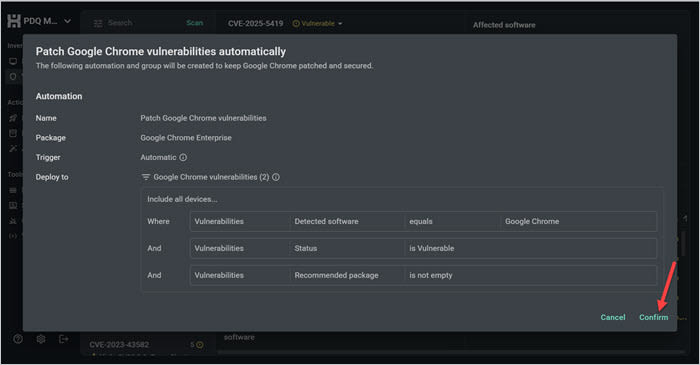
3. Now click the Automations tab, and you’ll see the newly created automation. Select it.
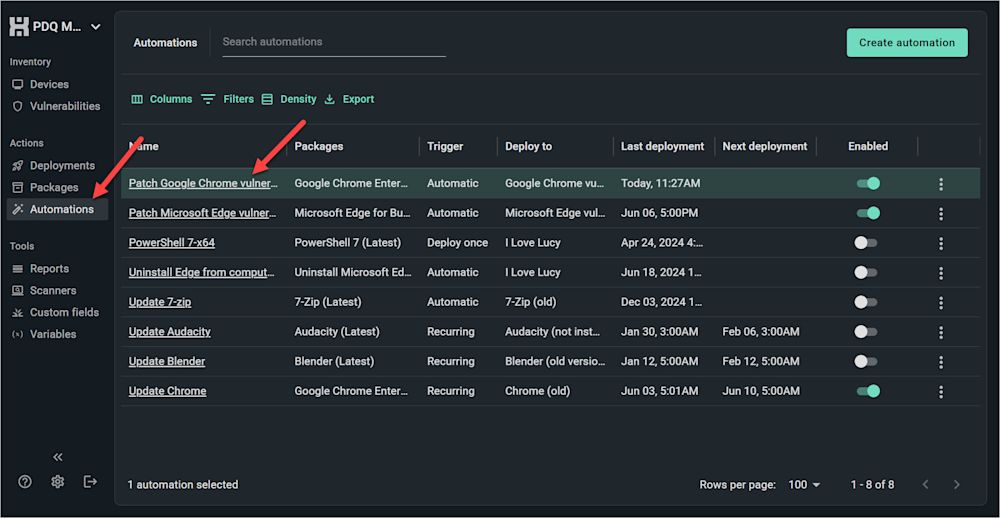
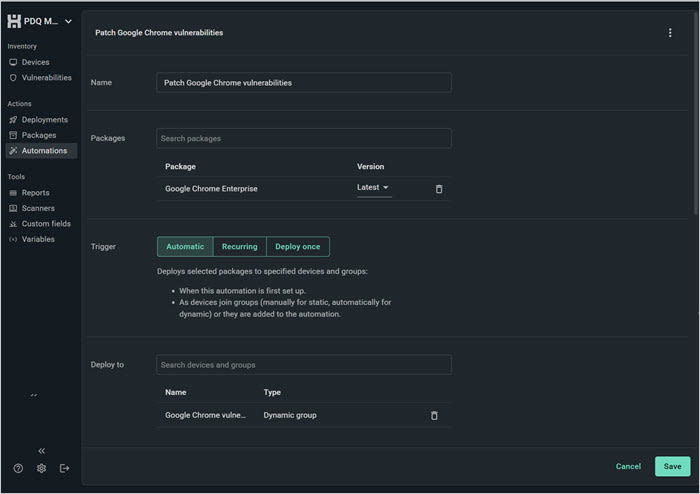
4. As you can see, the automation is set up to run automatically and deploy the latest version of Chrome to devices with a vulnerable version. However, we can adjust the trigger, version, or group based on our needs.
Automated vulnerability patching FAQ
What are the benefits of automating vulnerability patching?
Automating the patching process can make it faster, easier, and just plain better. It often improves:
Speed: Apply security updates quickly.
Consistency: Patch all systems the same way.
Compliance: Meet audits and regulations easily.
Risk reduction: Close gaps before attackers find them.
Automation turns vulnerability patching from a five-alarm fire into a smooth, repeatable process.
"It's limiting the number of conversations that you do have to have." — Josh Mackelprang, PDQ Senior Director, IT & Security — IT and InfoSec: Why it feels like a turf war (and how to fix that)
What’s the difference between automated patch management and automated vulnerability management?
Like the difference between patch management vs. vulnerability management, automated patch management applies software updates to fix security weaknesses, whereas automated vulnerability management identifies and prioritizes security weaknesses. While vulnerability tools scan and report, patch tools remediate vulnerabilities by deploying updates. PDQ Connect combines both types of tools to streamline the process.
Why use automated patch management software for vulnerability remediation?
Automated patch management software with built-in remediation can address vulnerabilities quickly by deploying relevant patches based on real-time scan results. This accelerates response time and improves cybersecurity.
How does automated vulnerability patching help defend against cyber threats?
By rapidly identifying and remediating known vulnerabilities, automated vulnerability patching reduces the attack surface threat actors can exploit. This proactive defense limits exposure to evolving cyber threats using real-time threat intelligence.
What’s the role of a security team in automated vulnerability patching?
While automation handles vulnerability scans and patch deployment, the security team defines patching policies, monitors patch status, and ensures remediation aligns with business risk. Human oversight is key to maintaining enhanced security and visibility. Automation works with you, not instead of you.
What tools support automated vulnerability patching?
The best tools for automated vulnerability patching combine built-in vulnerability scanning and automated deployment. These features work together to speed up patching and reduce the risk of human error.
Can automated patching handle all software vulnerabilities?
Unfortunately, automated patching can’t handle every potential software vulnerability. Automation can help with many CVEs, particularly those with available security patches. However, some critical vulnerabilities may still call for a manual patch management process due to system constraints, patch conflicts, or custom software environments.
Automating vulnerability management saves you time and locks down your security posture. It’s one of those mythical win-win scenarios — like finding twenty bucks and a fully intact Kit Kat in last winter’s hoodie. Or scoring a free trial of PDQ Connect and becoming the most powerful sysadmin you’ve ever known.




