Windows Remote Management (WinRM) lets you run PowerShell commands on remote Windows devices. If it's not enabled, remote scripting won’t work. Here’s how to check if WinRM is enabled and how to turn it on using several common methods.
Easily run PowerShell scripts on remote devices
Need to run your awesome PowerShell scripts on remote devices? PDQ Connect can easily execute PowerShell scripts on any managed device with an active internet connection.
How do you check if WinRM is enabled?
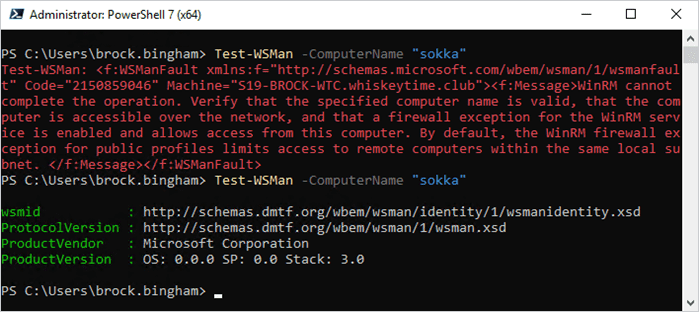
Before we start configuring WinRM, it’s a good idea to check to see if it’s already enabled on your devices. To test if WinRM is enabled, run Test-WSMan from a PowerShell window. Here’s an example.
In this guide, I’m using PowerShell 7.x from an elevated command prompt. These commands should also work in Windows PowerShell, though you can get different results if you are using a mixture of Windows PowerShell and PowerShell 7.x on your devices.
Test-WSMan -ComputerName “computer_name”
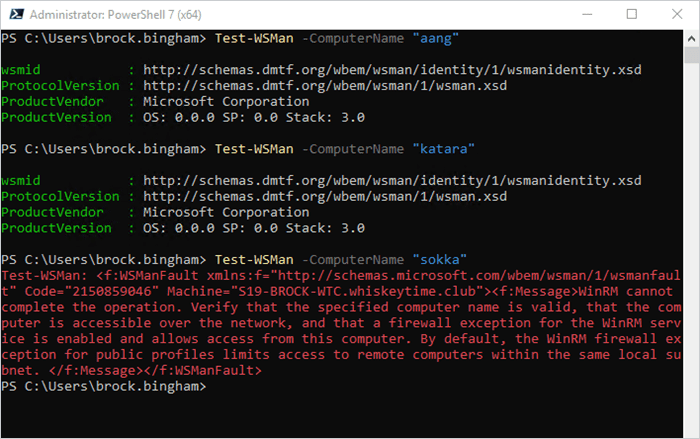
I ran this command on a few different computers, two with WinRM enabled and one with it disabled so you can see the different results. This command is great if you’re like me and your biggest pet peeve is doing extra work for no reason.
How do you enable WinRM using quickconfig?
The fastest and easiest way to enable WinRM is with the WinRM quickconfig command. WinRM quickconfig automatically configures several settings, such as WinRM listeners, inbound firewall rules, and the Windows Remote Management (WS-Management) service, to ensure WinRM is working properly.
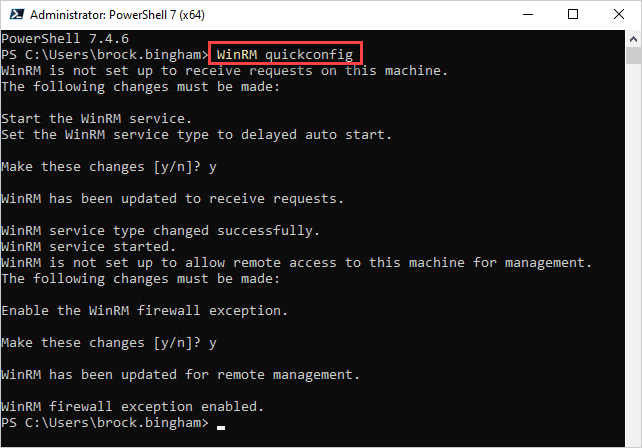
In this screenshot, you see that the command walked me through several prompts, enabling the various settings to ensure WinRM is properly configured. Now if we rerun the test from the previous section, this device should pass it.
While this command is very fast and easy to use, it does have a couple of drawbacks. First, since WinRM isn’t already enabled on the target devices, you’ll need to run the command locally on the client computer or run a remote PowerShell session with something like PsExec to run the command. Second, this method is only quick if you need to enable WinRM on a few machines. If you need to enable WinRM on dozens of devices or across an entire domain, you’ll want to use one of the methods discussed below.
How do you enable WinRM using Group Policy?
Group Policy is a great option for enabling WinRM in a domain environment. With Group Policy, you can quickly enable WinRM, configure the WinRM service, and set your firewall rules. Group Policy also has several other features you can configure to customize your WinRM implementation.
Here’s how to enable WinRM with Group Policy and set the IP filters.
Open your Group Policy Management Console.
Right-click on an OU you want to apply the policy to, then click Create a GPO in this Domain, and Link it here.
Name the policy Enable WinRM, then click OK.
Right-click on the new GPO and click Edit.
Expand Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Remote Management (WinRM) > WinRM Service.
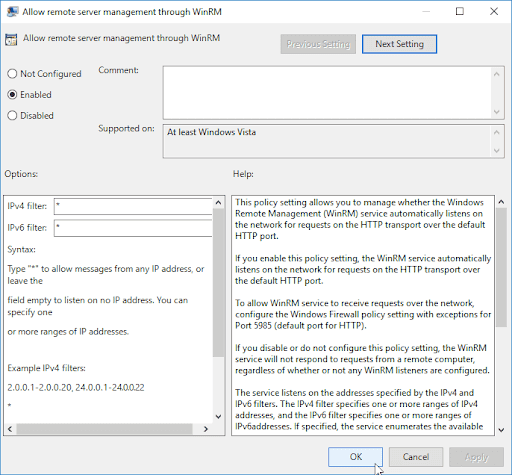
Locate Allow remote server management through WinRM, and double-click it to edit the setting.
Select Enabled.
Enter a range of IP addresses in the IPv4 and IPv6 filter boxes or add an asterisk to allow all IP addresses.
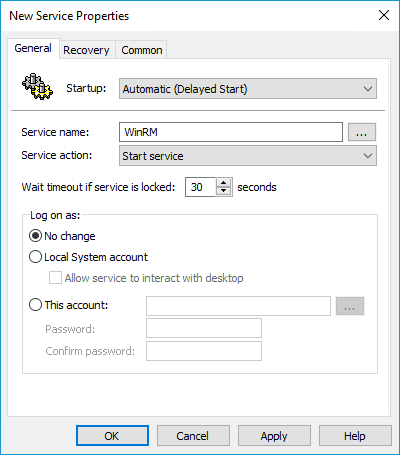
Next, let’s configure the WinRM service to start automatically.
Navigate to Computer > Configurations > Preferences > Control Panel Settings > Services.
Right-click in the Services window, then click New > Service.
Change the Startup to Automatic (Delayed Start).
Click the ellipsis button next to the Service name field.
Find and select the service name WinRM.
Select Start Service from the service action menu, then click Apply and OK.
Finally, we need to configure the firewall rules.
Expand Computer Configuration > Policies > Windows Settings > Security Settings > Windows Defender Firewall with Advanced Security > Windows Defender Firewall with Advanced Security.
Right-click on Inbound Rules, then click New Rule.
Select Predefined, then select Windows Remote Management from the drop-down menu.
Click Next.
Uncheck the public profile rule.
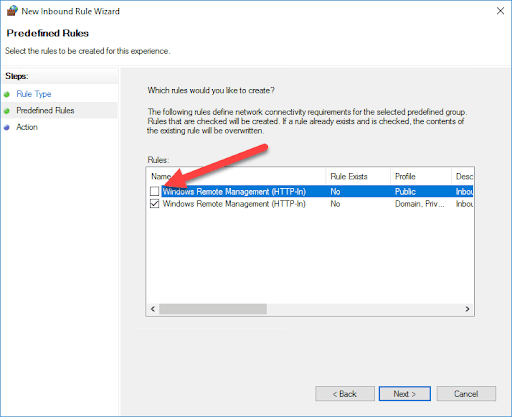
Click Next.
Select Allow the connection, then click Finish.
With the Group Policy Object in place, any devices assigned that GPO will automatically have the necessary Windows Remote Management settings configured.
Can you use PDQ Connect to enable WinRM?
You can use PDQ Connect to enable WinRM. Doing so gives you the ability to deploy the package to remote devices. To create a WinRM enablement package in Connect:
Click the Packages tab.
Click Create package.
Add a package name.
Click the down arrow next to Add install step, then click Add script step.
In the PowerShell window, enter the command
WinRM quickconfig -quiet.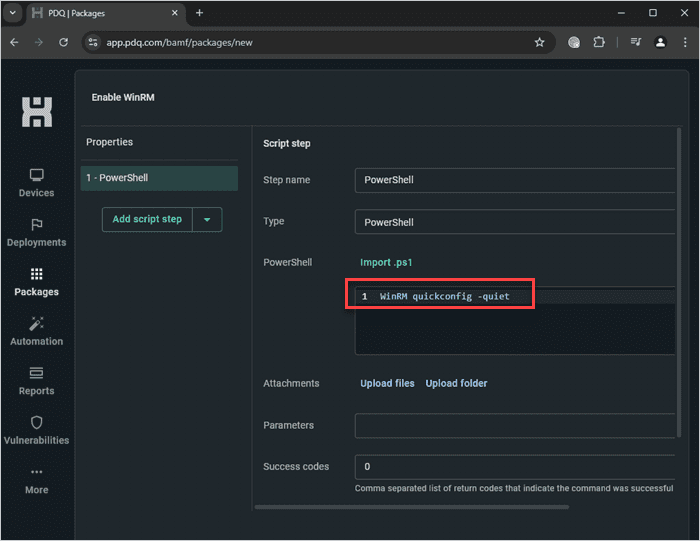
When you’re ready, click Save to save the package.
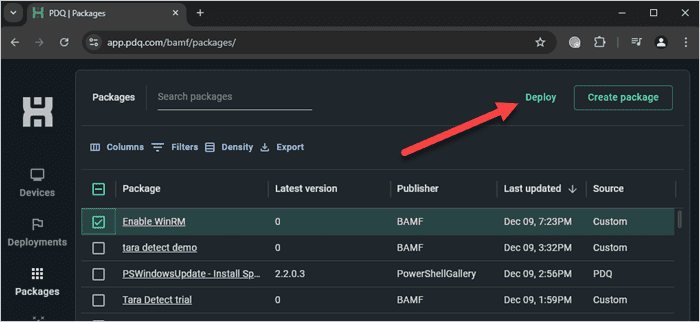
To deploy the package:
In the Packages tab, locate and select the package you just created, then click Deploy.
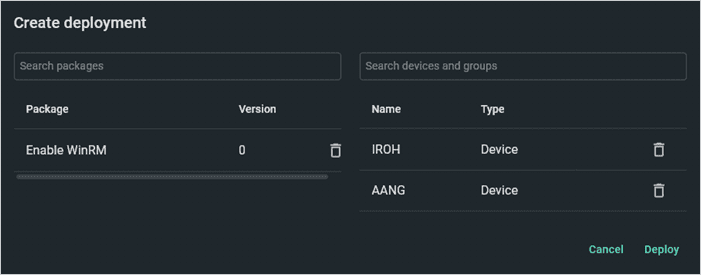
Add your target devices or groups by searching for them in the Search devices and groups field.
When you’re ready, click Deploy.
Keep in mind that while PDQ Connect can deploy packages over the internet, WinRM still requires that target devices be reachable on your local network.
WinRM is pretty cool, but not quite that cool.
Can you use PDQ Deploy to enable WinRM?
PDQ Deploy lets you push the WinRM quickconfig command to any device on your local network, making it ideal for on-prem deployments. To ensure we don’t interrupt any users, we’ll use the -quiet parameter to run the command silently.
In PDQ Deploy, click New Package.
Add a name like Enable WinRM to your package.
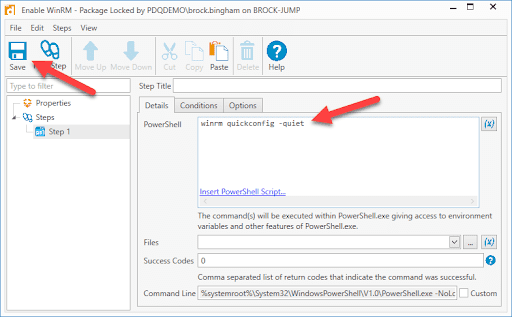
Click New Step > PowerShell.
Add the command
WinRM quickconfig -quietto the PowerShell window.Click Save.
Your WinRM package is ready to deploy to as many or as few devices as you need. This is a great way to limit the number of devices you enable WinRM on.
Whether you’re enabling WinRM on one machine or wrangling an entire domain, the right tool can save you a heap of time and coffee. PDQ Connect makes it easy to deploy scripts like WinRM quickconfig across remote devices — no VPN required. Try PDQ Connect for free and see how simple remote device management can be when the software actually works with you, not against you.
How to enable WinRM FAQs
What is WinRM used for?
WinRM (Windows Remote Management) lets you run PowerShell commands on remote Windows devices. It’s commonly used for remote scripting, automation, and configuration tasks.
Is WinRM secure?
WinRM uses HTTP by default, but it can be configured to use HTTPS for encrypted communication. It's secure when you pair it with authentication, encryption, and proper IP filters or firewall rules.
What are the default ports for WinRM?
By default, WinRM listens on port 5985 for HTTP and 5986 for HTTPS.