As cyberattacks increase in both frequency and severity, they have taken center stage in the changing world of cybersecurity. While keeping threat actors out of your environment is absolutely critical, I believe that keeping coworkers out of your embarrassingly large private stash of pirated Golden Girls episodes is at least mildly important.
Thankfully, keeping your private stash and company secrets safe is pretty straightforward with file and folder permissions. Here’s how you can go about securing your most important assets with ICACLS.
What is ICACLS?
ICACLS, which stands for Integrity Control Access Control List, is a command-line utility for managing file and folder permissions. While the manual process of managing permissions is easy enough, it becomes tedious — if not impossible — when you have a multitude of permissions to set. That's the perfect use case for ICACLS, which allows us to script out these larger jobs in bulk.
Manage permissions via Windows Explorer
Managing permissions through Windows Explorer is pretty easy. Simply right-click on any file or folder and click Properties, then click on the Security tab.
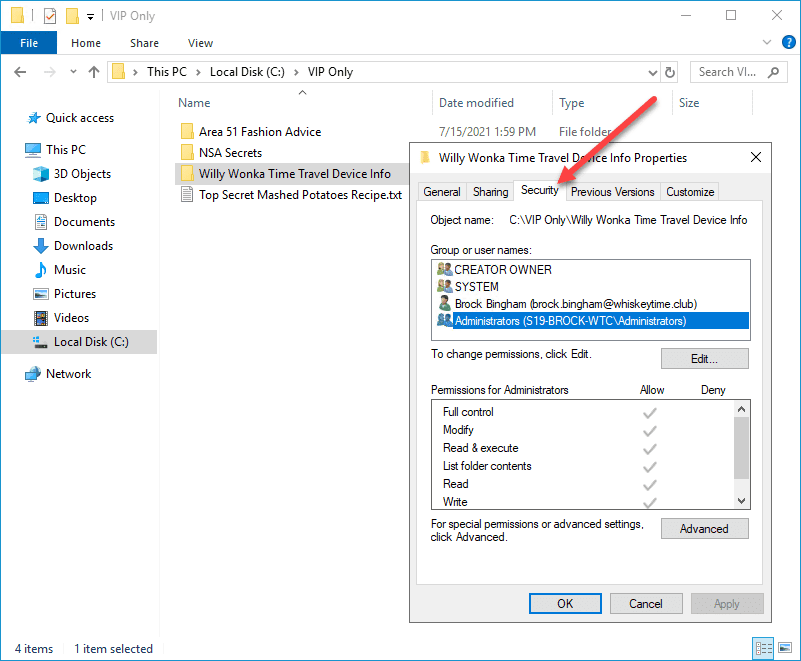
While this is relatively simple to do, you’ll start to run into issues when you have massive amounts of permissions to set. Thankfully, with the ICACLS utility, we're able to script out larger permissions jobs.
The PowerShell equivalent of ICACLS
The PowerShell equivalent of ICACLS is Get-Acl and Set-Acl:
NAME
Get-Acl
SYNTAX
Get-Acl [[-Path] <string[]>] [-Audit] [-AllCentralAccessPolicies] [-Filter <string>] [-Include <string[]>]
[-Exclude <string[]>] [-UseTransaction] [<CommonParameters>]
Get-Acl -InputObject <psobject> [-Audit] [-AllCentralAccessPolicies] [-Filter <string>] [-Include <string[]>]
[-Exclude <string[]>] [-UseTransaction] [<CommonParameters>]
Get-Acl [-LiteralPath <string[]>] [-Audit] [-AllCentralAccessPolicies] [-Filter <string>] [-Include <string[]>]
[-Exclude <string[]>] [-UseTransaction] [<CommonParameters>]
ALIASES
None
REMARKS
Get-Help cannot find the Help files for this cmdlet on this computer. It is displaying only partial help.
-- To download and install Help files for the module that includes this cmdlet, use Update-Help.
-- To view the Help topic for this cmdlet online, type: "Get-Help Get-Acl -Online" or
go to https://go.microsoft.com/fwlink/?LinkID=113305.NAME
Set-Acl
SYNTAX
Set-Acl [-Path] <string[]> [-AclObject] <Object> [[-CentralAccessPolicy] <string>] [-ClearCentralAccessPolicy]
[-Passthru] [-Filter <string>] [-Include <string[]>] [-Exclude <string[]>] [-WhatIf] [-Confirm] [-UseTransaction]
[<CommonParameters>]
Set-Acl [-InputObject] <psobject> [-AclObject] <Object> [-Passthru] [-Filter <string>] [-Include <string[]>]
[-Exclude <string[]>] [-WhatIf] [-Confirm] [-UseTransaction] [<CommonParameters>]
Set-Acl [-AclObject] <Object> [[-CentralAccessPolicy] <string>] -LiteralPath <string[]>
[-ClearCentralAccessPolicy] [-Passthru] [-Filter <string>] [-Include <string[]>] [-Exclude <string[]>] [-WhatIf]
[-Confirm] [-UseTransaction] [<CommonParameters>]
ALIASES
None
REMARKS
Get-Help cannot find the Help files for this cmdlet on this computer. It is displaying only partial help.
-- To download and install Help files for the module that includes this cmdlet, use Update-Help.
-- To view the Help topic for this cmdlet online, type: "Get-Help Set-Acl -Online" or
go to https://go.microsoft.com/fwlink/?LinkID=113389.As you can see, Microsoft has chosen to stick with their noncreative but very descriptive naming schemes with these cmdlets. One look and you can pretty easily guess what each one does. As their names imply, Get-Acl retrieves the access-control list of a given file or folder. Set-Acl, on the other hand, sets or modifies the permissions of files and folders.
Okay, time for some examples.
Example 1: Viewing permissions
DIR 'path(filter)' -Recurse | Get-Acl | Format-List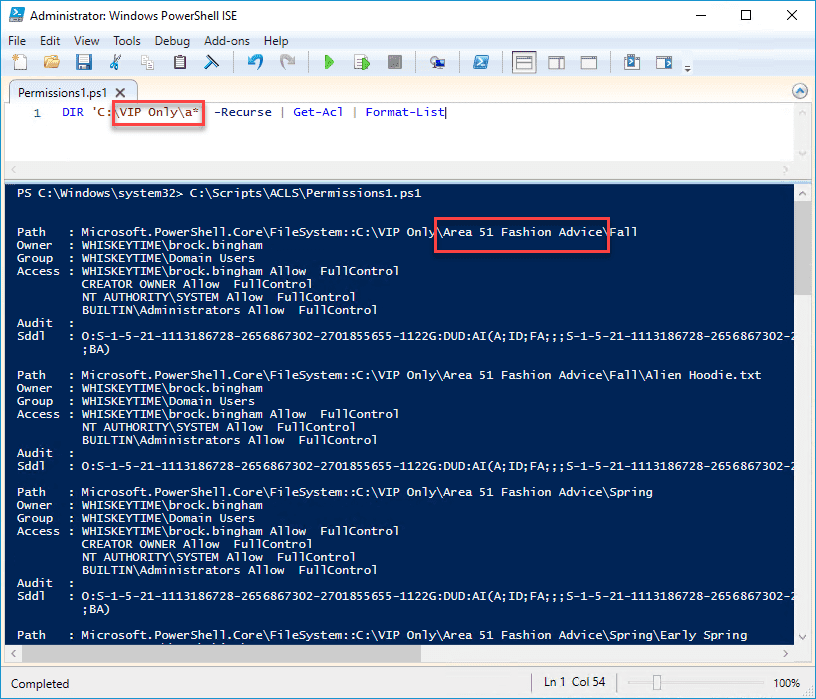
We're starting off pretty simple, but there's still some cool stuff going on here.
We've used the DIR command and specified the path 'C:\VIP Only\' with the filter a*. The only folder inside the "VIP Only" folder that matched the filter was a folder named "Area 51 Fashion Advice". We've used the -Recurse parameter to return all subdirectories and files. Be careful using this parameter on a folder that has large amounts of subdirectories and files, though.
Next, we piped that command to the Get-Acl command, returning the permissions for all the files and folders found in the specified directory. Lastly, we piped everything to the Format-List command to make the returned information a bit easier to read.
Example 2: Copying permissions
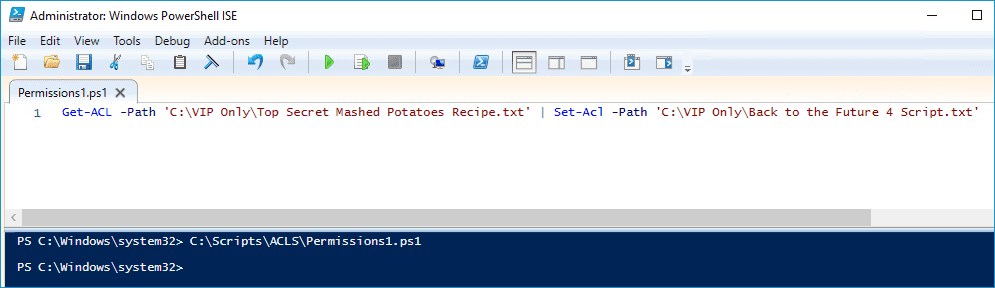
Get-Acl -Path 'Path1 | Set-Acl -Path 'Path2'We are using both Get-Acl and Set-Acl to copy the permissions from one file to another in this example.
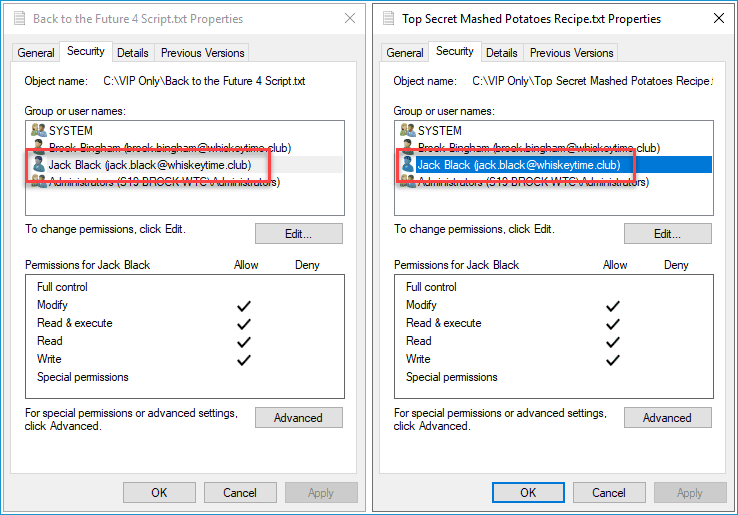
I have a file called “Top Secret Mashed Potatoes Recipe.txt” and a "Back to the Future 4 Script.txt" file in the same "VIP Only" directory. As you can see, the user Jack Black currently has permissions on one file but not the other.
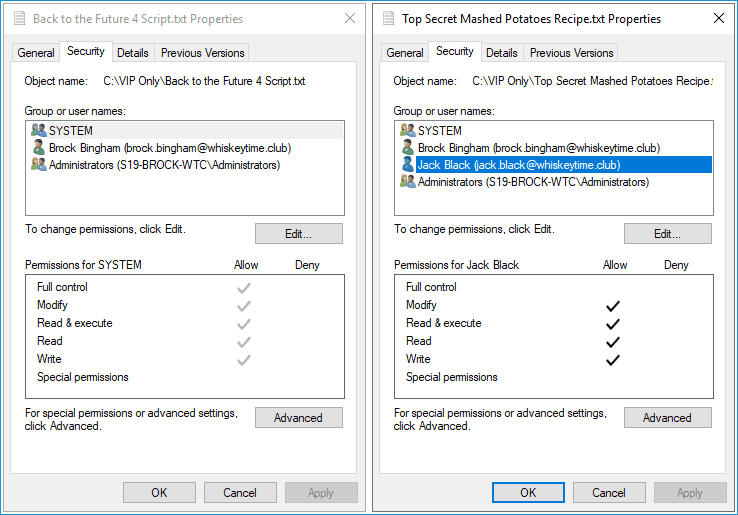
However, once I run the above script, PowerShell copies the permissions from "Top Secret Mashed Potatoes Recipe.txt" to "Back to the Future 4 Script.txt."
Example 3: Setting permissions
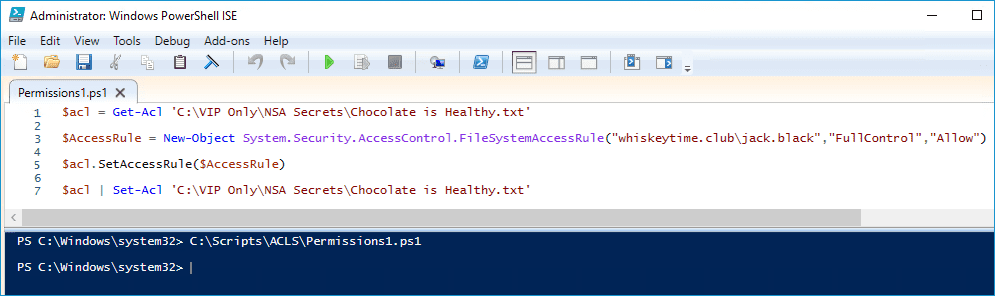
$acl = Get-Acl 'path'
$AccessRule = New-Object System.Security.AccessControl.FileSystemAccessRule("username","permission","allow or deny")
$acl.SetAccessRule($AccessRule)
$acl | Set-Acl 'path'The first two examples were pretty simple. However, setting permissions is a bit trickier than just getting or copying permissions.
In this example, the first thing we do is retrieve the ACL of the object we want to modify and assign it to the variable $acl. Next, we create a new file system access rule and assign it to the $AccessRule variable. This rule contains the "username", the "permission", and the "allow or deny" settings. Then, we set the access rule we created to the $acl variable. Lastly, we use the Set-Acl cmdlet to set the new permissions contained in the access rule.
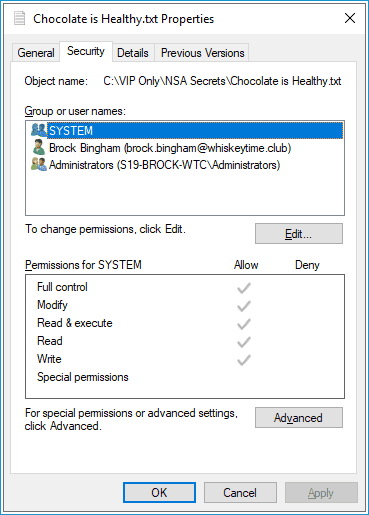
As you can see in this image, the file "C:\VIP Only\NSA Secrets\Chocolate is Healthy.txt" doesn't have permissions for the user Jack Black.
However, once I run the following script, the user's permissions are added to the file and granted full control.
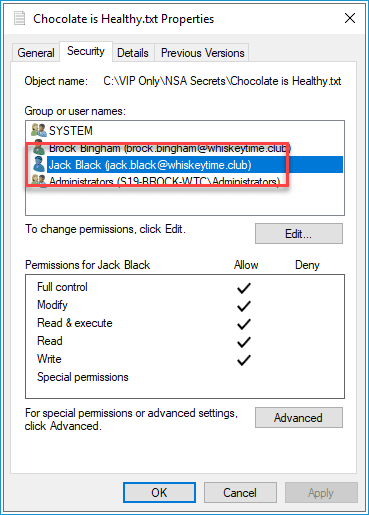
Magic!... I mean, PowerShell! (Same thing, right?)
Ready to write your own PowerShell scripts?
Check out our four-step guide on how to write and run a PowerShell script.
PowerShell vs. ICACLS: Which should you use?
I'll be honest. I find it easier to set permissions with ICACLS versus Set-Acl. However, there are limitations with ICACLS, whereas the possibilities are almost limitless with PowerShell. If you have some simple permissions to set, I would use either Windows Explorer or ICACLS. If, on the other hand, you have an enormous amount of permissions to set and you need to automate a workflow, PowerShell should be your go-to.
Looking for an impressive gallery of go-to PowerShell cmdlets?
Prepare to be amazed. The nerdiest nerds here at PDQ rounded up the best PowerShell cmdlets around. Check out our gallery of PowerShell commands.