A virtual private network (VPN) is a secure, encrypted connection to the internet that protects your data and hides your IP address, especially on public Wi-Fi.
Using an unsecured network may expose your online activity to strangers. They could access your browsing history, see what links you clicked, check your downloaded files, and intercept other data. You may feel like you’re living the dream as you sip a comically large iced coffee while going through your company’s financial records, but you might be in for a rude awakening if you’re using the coffee shop’s unsecured Wi-Fi network.
A VPN can help you get your caffeine fix with less risk. It encrypts your data, essentially scrambling it to make it unreadable to prying eyes. Even your internet service provider (ISP) can’t decipher what you’re doing. At the same time, the VPN connection hides your IP address for greater anonymity. Sure, everyone at the coffee shop may recognize you from your rare quintuple shot of espresso, but at least they won’t know you by your IP address.
We’ll explain the basics of VPNs, including how they work, common protocols and VPN types, potential alternatives, and how to choose the best virtual private network for your business.
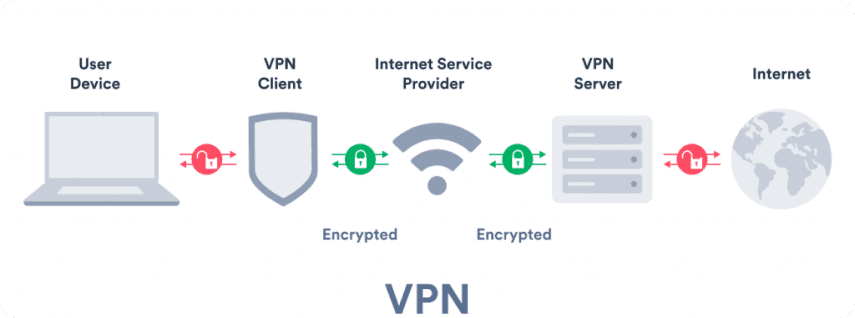
How does a VPN work?
VPN technology works by creating a secure VPN tunnel through which you can send and receive data. The process breaks down into distinct steps:
Sending data
Connecting to the server: When you turn on your VPN service, the VPN client (software app) connects to a VPN server. That VPN server then becomes an intermediary between your device and other external servers.
Encryption: The VPN client or extension encrypts the data and sends it to the VPN server.
Download: The VPN server downloads the data.
Decryption: The VPN server decrypts the data and sends it to the intended recipient.
Receiving data
Connecting to the server: The VPN client connects to a VPN server.
Download: The VPN server downloads the data you’re trying to access.
Encryption: The VPN server encrypts the data.
Decryption: The VPN client or extension decrypts the data to allow you access.
While these processes may appear time consuming, they usually occur in a fraction of a second. Modern CPUs use the Advanced Encryption Standard (AES) instruction set to improve the speed and security of applications, which enhances throughput of encrypted data.
What are common VPN protocols?
Virtual private network protocols govern how data is transmitted and encrypted along its journey. Some services allow you to select protocols based on your needs. Each has potential benefits and drawbacks.
PPTP: Originally built by Microsoft to tunnel dial-up traffic, Point-to-Point Tunneling Protocol (PPTP) is the earliest common VPN protocol. PPTP is fast and highly compatible, but it is not particularly secure. With relatively weak encryption protocols and abundant vulnerabilities, most VPNs prefer other protocols.
IPsec: Internet Protocol Security (IPsec) is a suite of protocols that work together to provide privacy, integrity, and authentication.
SSL: Secure sockets layer (SSL) generally runs through a web browser for easy management. An SSL VPN allows access to web-enabled SSL applications but not physical resources, like printers.
L2TP: Layer 2 Tunneling Protocol (L2TP) is a VPN tunneling protocol used to create a connection. It must be paired with another protocol for data encryption. It’s quite secure, but encapsulating data twice leads to slower performance.
OpenVPN: OpenVPN is an open-source, highly secure protocol. It uses strong encryption, but it has slower speeds than some options.
SSTP: Created by Microsoft, Secure Socket Tunneling Protocol (SSTP) integrates well with Microsoft operating systems. It provides a moderate level of security and faster speeds than some protocols.
IKEv2: Internet Key Exchange version 2 (IKEv2) was developed by Microsoft and Cisco to provide an authenticated, encrypted connection that’s fast, stable, and secure.
WireGuard: This open-source protocol is a newcomer, but it’s quickly gaining popularity for its speed and advanced cryptography. However, it is still considered experimental.
What are the different types of VPNs?
While businesses often favor remote access or site-to-site VPNs, several options are available. Depending on your business needs, any of these varieties may be appropriate.
Remote access VPN
Remote access VPNs connect users to a private network, allowing them to access it from a remote location. For businesses, this may be a powerful tool to help employees access company resources while working from home or on the road. At the same time, a remote access VPN also protects data so that users can connect safely via a public network.
Personal VPN service
Personal VPNs connect the user to the internet via an intermediary server that encrypts the connection. They’re popular with consumers looking to hide their IP address, protect their online privacy, access geographically restricted content, and evade censorship.
Mobile VPN
Mobile VPNs give users private internet access, even if their connection is unstable or they change networks during the session. This may make them ideal for businesses with mobile workers (delivery drivers, repair technicians, etc.) or employees who work from home in areas with poor connectivity.
Site-to-site VPN
Also known as network VPNs, site-to-site VPNs connect disparate networks, effectively creating a single network despite physical distance.
Intranet-based VPNs: An intranet-based VPN connects networks that belong to the same company, allowing companies with multiple offices to use the same resources.
Extranet-based VPNs: An extranet-based VPN connects two independent companies. It may be useful for connecting to the network of a supplier or another close partner.
What are the differences between a free VPN and a paid VPN?
As the names suggest, a free VPN app is available without charge, while a paid VPN carries a fee. However, these two options vary in more than just price points.
Speed: Any VPN may slow your connection speed, but the effect is likely to be more significant when using a free VPN app.
Bandwidth: Free VPNs often have bandwidth limits, so you may have to turn it on and off to ensure you have service when you need it most. On the other hand, paid VPN services are frequently unlimited.
Privacy: Free VPNs may sell your personal data and browsing history. Some free VPNs have even been known to redirect you to a partner’s website unprovoked.
Security: Paid services typically use stronger VPN encryption, making it harder for threat actors to access private information while it’s in transit. A free VPN’s server infrastructure may leave something to be desired, potentially exposing your data.
Server locations: Paid VPNs usually have extensive server networks, allowing you to access options closer to your location for greater speed.
Ads: Even free VPNs need to turn a profit somehow. Many services use ads to do so. Not only can this slow performance, but it can also be super annoying. To make it even worse, some could even infect your computer with malware. Ironic, right?
Are there any alternatives to using a VPN?
VPNs are popular, but several alternative technologies offer similar or even stronger protections depending on your network architecture and security goals. Several alternatives provide similar benefits to VPNs, and many businesses prefer these options to accommodate an increasingly remote workforce. Some companies also use these to supplement VPNs.
Proxy server
A proxy server relays traffic from your device to the website you’re trying to visit. It works at the application level to hide your IP address. However, it does not provide an encrypted tunnel, making it less secure than a VPN.
ZTNA
Zero-trust network access (ZTNA) is a concept rather than a product, but many solutions define themselves by the approach. ZTNA does not automatically trust any user, device, or network with access to resources. It relies on the principle of least privilege, the assumption of breach, and explicit verification. Applications are not visible to the public and are hidden from discovery. This approach is scalable, limits the attack surface, and allows granular-level control.
SDP
Sometimes used interchangeably with ZTNA, a software-defined perimeter (SDP) creates a network perimeter based on software instead of hardware. This hides the servers, routers, and any other network-connected infrastructure from external sources. Access is granted to users after verifying their identity and assessing their device. Then, the VPN user has their own network connection with access to approved services.
SD-WAN
A software-defined wide area network (SD-WAN) uses a virtual WAN architecture free from a traditional router system. It centralizes the management of multiple WAN links and optimizes traffic routing based on application requirements. This scalable, flexible solution is designed to support cloud-based environments and applications in addition to on-premises data centers across physical locations.
SASE
Secure access service edge (SASE) combines ZTNA, SD-WAN, firewall as a service (FWaaS), secure web gateway, and a cloud access security broker (CASB) into a single cloud-based tool. It can simplify your infrastructure, enhance your flexibility, improve performance, and help you save money.
Are VPNs safe?
Premium VPNs are usually safe. While a VPN could be hacked, the use of cryptography enhances the overall confidentiality, authentication, and message integrity. That said, companies also need additional security measures to maintain a strong posture.
Users should be aware that some free VPNs undermine security rather than enhance it. Thoroughly researching any solution before you try it can help prevent you from making costly mistakes by trying to save money.
Also, pay attention to pertinent local laws. VPNs are legal in the United States, but they are illegal or restricted in select countries, including Belarus, China, Egypt, Iraq, North Korea, Oman, Russia, Turkey, Turkmenistan, Uganda, and the United Arab Emirates.
Who uses VPNs?
Anyone concerned with privacy or interested in accessing geographically restricted content might use a VPN. Approximately 85% of adult internet users are aware of VPNs, and 49% use them. Here are a few common reasons people cite for using a VPN:
Maintaining anonymity while browsing
Accessing work-related resources
Consuming entertainment content
Using social networks, websites, and news
Communicating with friends and/or family abroad
Keep in mind that some websites block traffic from known VPN IP addresses, so using a VPN can prevent these sites from loading. Financial institutions and some streaming services recently started blocking traffic from VPNs because these services prefer to validate the source.
Why would a business use a VPN?
VPNs offer several potential benefits for businesses:
Secure remote access
A VPN allows employees to connect remotely to your office network, enabling them to access company resources. For work-from-home and hybrid arrangements, a VPN can be critical to collaboration.
Access control
By verifying required credentials, a VPN acts as access control to allow the right people and applications to get what they need while preventing the wrong ones from reaching private data.
Cybersecurity
Shielding your internet activity can be invaluable for cybersecurity. When you connect via a public network, it’s remarkably easy for threat actors to intercept your traffic, making a VPN especially useful. However, it can be beneficial even on a private network.
The VPN acts as a barrier between your network and the broader internet. Masking your IP address can help reduce the likelihood of attacks that rely on knowing your location, such as man-in-the-middle (MITM) attacks, remote hacking, and distributed denial of service (DDoS) attacks.
How do you choose the right VPN for your business?
The best VPN for your business depends largely on your needs and goals. Assessing key aspects of a VPN service can help you make an informed decision.
Consider the following:
Server details
VPN providers vary in the location and quantity of their servers. Having more servers generally leads to a faster experience since users are spread out. Similarly, accessing a server closer to your physical location can improve speeds. If you need an IP address in a specific country, you’ll also want to confirm that any VPN provider you consider has a server there.
Speed
Many VPN providers advertise their speeds, but looking at third-party test results may give you a more accurate idea of what to expect.
Service level
Premium services typically offer greater stability, speed, security, and privacy than free versions.
Protocols
VPN protocols vary in speed, security, encryption, ease of use, and stability. You should confirm that the VPN software you’re considering uses protocols that meet your needs.
Device coverage
With mobile devices accounting for over half of internet traffic, a VPN may be just as critical for your employees’ cell phones as their laptops and desktops.
OS compatibility
To work, the VPN must be compatible with your operating system.
Features
VPNs may include a wide range of features, including:
Kill switch: If the connection between your device and the VPN server is interrupted, it can put you at risk. A kill switch automatically shuts down your internet connection if this occurs.
No-log policy: Logging data means the VPN software maintains records of your activities, which may include your browsing history, connection times, IP address, and more. Therefore, a VPN provider with a no-log policy may be better equipped to offer more complete privacy.
No bandwidth limits: Some VPNs have bandwidth limits. If you exceed those limits, the provider may throttle your bandwidth.
Ad blocker: Ads can be a thorn in any internet user’s side. An ad blocker helps prevent ads and trackers to save you the annoyance (and the temptation to buy the latest fad products).
IP address sharing: When a VPN groups users on a shared IP address, it can enhance everyone’s security by making it more difficult to identify one user’s actions. There’s safety in numbers.
Reputation
You’re trusting your VPN provider with your business’s privacy and security, so reputation matters. Consider customer and professional reviews, and know who you’re working with.
Support
When something goes wrong, an expert support team can make a world of difference. (That’s why PDQ maintains one of the best support teams around.) Assessing the VPN provider’s support options before embarking on a long-term relationship with them can save you time and headaches down the road.
Understanding what a VPN is, and isn’t, can help you make smarter decisions about your network security, especially in today’s remote and hybrid work environments. Whether you're locking down company traffic or just trying to stay anonymous at your local coffee shop, a VPN is a simple but powerful tool.
Still have questions or want to hear how other IT pros are handling their setups? Join our PDQ Community or hang out with us on Discord to swap tips, get advice, and connect with folks who speak fluent sysadmin.



