A strong corporate password policy should be clear, enforceable, and easy for employees to follow. Our downloadable password commandments PDF and this guide give you a ready-to-use baseline for building stronger credentials across your organization and effective password management.
Use this PDF along with the following blog post as your ready-to-use baseline for smarter, stronger credentials across your org.
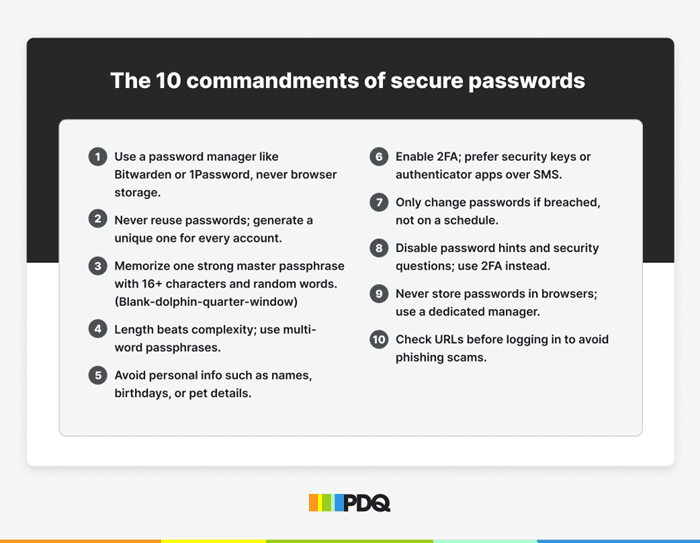
1. Use a password manager — not your browser’s “helpful” memory
Let’s start with the obvious: If your users are storing passwords in their browsers, you might as well be writing them on a sticky note labeled "Hack me." Browser-based storage is convenient, yes — but also vulnerable. Instead, use a dedicated password manager like Bitwarden or 1Password. They encrypt everything, support MFA, help users generate unique passwords, and store multiple passwords without the usual mental gymnastics.
Bonus: Most password managers also make onboarding and offboarding way easier. One click to remove access beats a scavenger hunt.
2. Never reuse passwords
Password reuse is like using the same key for your house, your car, and your bike lock — if someone grabs it, they’ve got access to everything. A strong password policy should always stress uniqueness so that one compromised password doesn’t spell certain doom. A password manager can generate a random, strong password for every login so users don’t default to "CompanyName2025!" across the board.
3. Memorize one strong master passphrase
This is the only password your users should need to memorize — the one that unlocks their password manager. Make it count. A long, random passphrase (like “socks-pickle-zeppelin-fence”) is easier to remember and much harder to crack than a short, complex password. This passphrase is the key to the kingdom. Treat it accordingly.
4. Use passphrases — password length > password complexity
For everything else, password length still rules. Whether it’s your computer login, VPN access, or anything outside your password manager, encourage users to choose multiword passphrases. They’re easier to remember, harder to guess, and play nice with your brain at 7:00 a.m. on a Monday.
Example: "potato-sky-folder-trombone" is exponentially more secure (and easier to remember) than "R3$0lut1on!"
5. Avoid personal info, like names, birthdays, or pets
Hackers love social media. They’ll try your dog’s name, your kid’s birth year, or your favorite team’s mascot in five seconds flat. Good password hygiene means skipping anything guessable — even if it’s cleverly spelled.
If it’s on Facebook, don’t put it in your password.
6. Enable MFA — and skip SMS when possible
Multifactor authentication is a must. It adds a second gate between attackers and your data. But not all MFA is created equal — prefer authenticator apps (like Microsoft Authenticator or Authy) or security keys over SMS, which can be intercepted via SIM swapping.
Rule of thumb: If you’re texting the second factor, assume someone else could read it too.
7. Only change passwords when there’s a reason
Forcing a password change every 30 or 60 days might feel secure, but users just end up cycling through weak passwords. NIST and Microsoft both recommend changing passwords only when there’s evidence of compromise — not on a schedule.
Scheduled changes or password expiration lead to users switching from common password to common password — like “Password1!” to “Password2!” to “Password3!” — which helps no one.
8. Disable password hints and security questions
Password hints are like leaving a key under the doormat and telling someone it’s under the mat. Password security questions (like “What’s your mother’s maiden name?”) aren’t much better — they’re easy to guess or find. If you need a backup access option, stick with MFA.
Pro tip: The best answer to “What’s your favorite color?” is “Use MFA instead.”
9. Don’t store passwords in browsers
Yes, this is worth repeating. Browsers prioritize convenience — not enterprise-grade encryption or access control. Your users might not realize it, but this is a big risk. If a device is compromised, stored passwords are often first on the shopping list.
Want convenience and security? Use a real password manager — not Chrome’s memory.
10. Check URLs before logging in to avoid phishing scams
Even strong passwords won’t help if you hand them over to a fake login page. Always verify the URL before entering credentials — especially if you got there via email. Look for HTTPS, avoid weird subdomains, and don’t click sketchy links when you’re running on two hours of sleep and bad coffee.
Security awareness training should teach your team to slow down and hover before they click. Phishing thrives on speed.
Wrapping it all up (and putting it into action)
The 10 commandments in the PDF aren’t just a checklist — they’re a strategy. Together, they can significantly reduce your risk of credential-based attacks while keeping the day-to-day user experience bearable.
Here’s how to turn this into an actual password policy that sticks:
Download the PDF
It’s your user-facing starter pack. Brand it, adjust it, own it.Share the “why” — not just the rules
This blog post helps you do just that. People follow what they understand.Train and test
Phishing simulations, password audits, and awareness campaigns help it all sink in.Enforce the easy stuff
Use policy enforcement tools, set minimum password requirements, and enable MFA org wide.Revisit the policy regularly
Technology evolves. So do threats. Make your policy a living document.
Keep endpoints patched & secure
Deploy custom or prebuilt software packages, automate maintenance tasks, and secure your Windows devices — no matter where they are.
Password policy best practices FAQs
What are the best practices for corporate password policies?
The top practices are:
Using a password manager
Never reusing passwords
Memorizing one strong master passphrase
Creating long passphrases
Avoiding personal info
Enabling MFA
Changing passwords only when necessary
Disabling hints and security questions
Not storing passwords in browsers
Checking URLs to prevent phishing
How often should corporate passwords be changed?
Passwords should only be changed when there’s evidence of compromise. Scheduled changes lead to weak variations like “Password1!” to “Password2!” which Microsoft and NIST password guidelines both advise against.
What type of multifactor authentication is best for corporate accounts?
Use authenticator apps or security keys instead of SMS. SMS MFA can be intercepted through SIM swapping, making it less secure.
Why are passphrases better than complex passwords?
Multiword passphrases are easier to remember and harder to guess. For example, “potato-sky-folder-trombone” is stronger than “R3$0lut1on!”
Should employees use browser password storage?
No. Browsers prioritize convenience, not enterprise-grade encryption. If a device is compromised, stored passwords are often the first to be stolen. A dedicated password manager is safer and more manageable.
Ready to go from “Yeah, we should do something about passwords” to “Our credentials are locked down tighter than a Y2K bunker”? Start with the PDF — and show your team that secure can be simple.