There’s a new vulnerability affecting billions of Intel processors codenamed Downfall. If your sysadmin sense has been tingling, it’s probably because the exposure impacts some of your devices — or you’ve had too much caffeine. Either way, here’s what you need to know about Downfall and how PDQ can help you identify affected devices.
What is Downfall?
Downfall is the latest in a string of unfortunate vulnerabilities affecting CPUs. Identified as CVE-2022-40982, Downfall takes advantage of memory optimization features built into specific Intel processors. Daniel Moghimi, the Senior Research Scientist at Google who discovered the vulnerability, wrote, “I discovered that the Gather instruction, meant to speed up accessing scattered data in memory, leaks the content of the internal vector register file during speculative execution.”
Threat actors could potentially use Downfall to access sensitive data such as passwords and encryption keys on vulnerable devices. Now, before you shut down your entire business operation in the name of cybersecurity, there is a bit of good news. Currently, the attack vector is local, meaning threat actors would already need access to a system to utilize Downfall.
However, cloud computing is another story. Cloud computing is designed to allow multiple users to utilize the same hardware resources simultaneously. While the big three (AWS, Azure, and Google Cloud) have already patched Downfall, you may want to ensure your cloud provider has taken the necessary steps to mitigate the risk.
What processors are affected by Downfall?
Unfortunately, most Intel processors manufactured between 2014 and 2021 are vulnerable to Downfall, meaning potentially billions of processors are at risk. This includes Intel’s 6th-gen Skylake Core through 11th-gen Tiger Lake Core processors and Xeon processors based on those same architectures.
Intel has released a comprehensive list of processors impacted by Downfall that people should definitely check out if they suspect their processor is vulnerable.
Identify computers vulnerable to Downfall with PDQ
One of the most important steps when remediating a vulnerability is quickly identifying the impacted devices. Without the right tools, this could involve hours of monotonous work and, even worse, lots of steps. However, I’ll show you how easy it is to identify at-risk devices with PDQ Inventory and PDQ Connect from the seclusion of your own office.
PDQ Inventory specializes in asset and data tracking for on-prem devices, while PDQ Connect specializes in managing remote devices. Try out both products free for 14 days.
Track impacted devices with PDQ Inventory
PDQ Inventory makes it easy to identify devices exposed to Downfall. With a custom dynamic collection, we can filter for vulnerable devices and quickly generate a report from the filtered results.
This example filters for Intel’s 6th – 11th generation Core-i3, i5, i7, and i9 processors and serves as a proof of concept. If you have Xeon or other impacted processors, add them to the collection filter.
This example filters for Intel’s 6th – 11th generation Core-i3, i5, i7, and i9 processors and serves as a proof of concept. If you have Xeon or other impacted processors, add them to the collection filter.
In PDQ Inventory, click New Dynamic Collection.
Name the filter.
Set the initial group filter to Any.
Add the filter: Hardware Device | Name | Contains | <processor_name>. In this example, I’ve followed the Intel naming convention to distinguish the different processors to filter for. Alternatively, you can download the collection's XML file and import it into your Inventory console. Ensure you modify the collection to meet the needs of your environment.
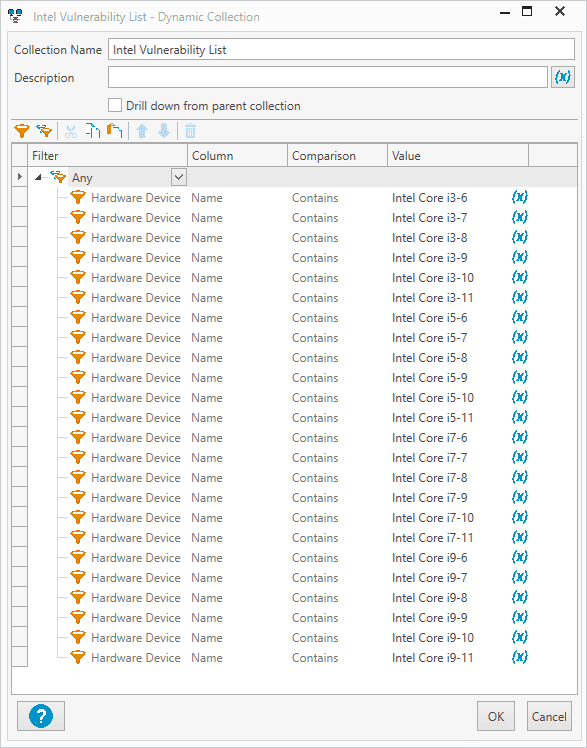
Add all the necessary filters for your devices, then click OK.
Devices that match the filter criteria will automatically populate into the collection. If you want to generate a report from this data, simply right-click on the collection, then click New > Report From Collection.
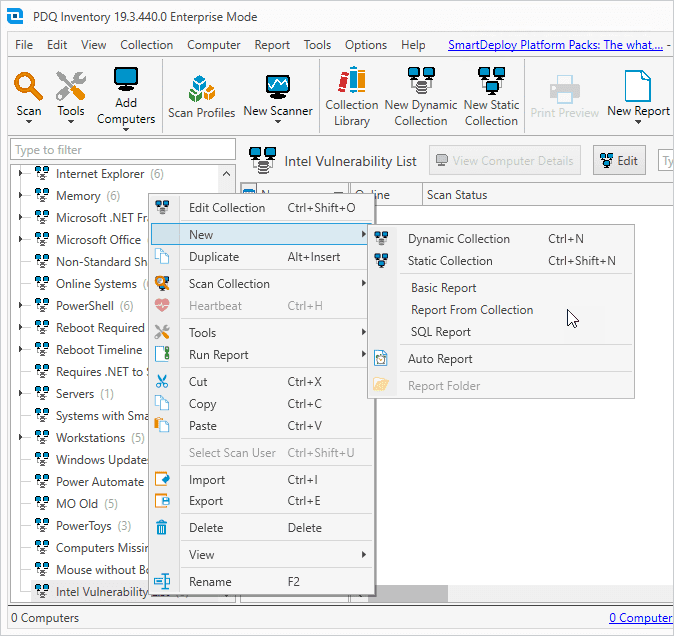
Identify vulnerable devices with PDQ Connect
With PDQ Connect, you can quickly identify vulnerable computers, including those hard-to-reach remote devices. While the process is similar to the process in PDQ Inventory, the device names are formatted a bit differently. Here’s how to create a group in PDQ Connect to identify Intel’s 6th – 11th generation Core-i3, i5, i7, and i9 processors.
In PDQ Connect, click the Devices tab.
Click Create group.
Add the filter: CPU | Name | contains | <processor_name>. Add additional filters with an ORstatement.
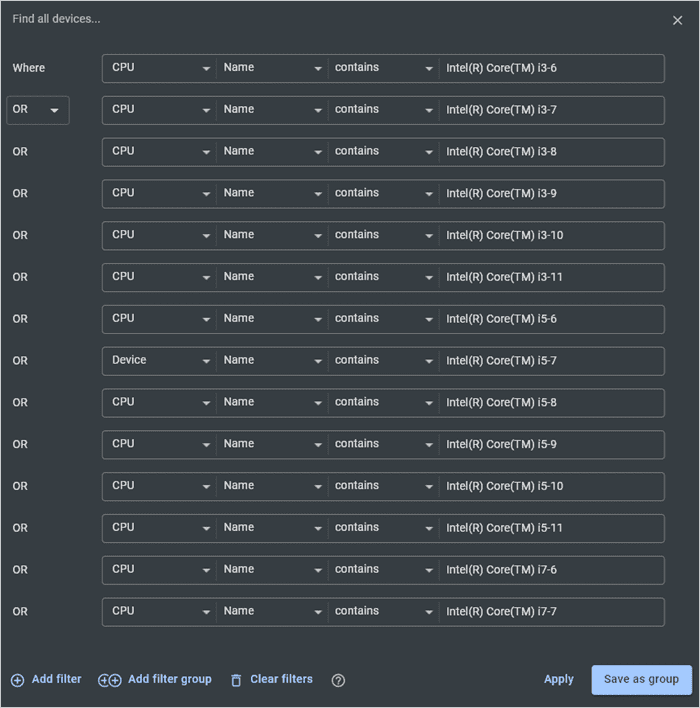
When you’re finished, click Save as group.
Name the group, then click Save.
The group will populate with a list of vulnerable devices. If you have other CPUs impacted by Downfall, such as vulnerable Xeon processors, add them to the group filters.
How to mitigate CVE-2022-40982
Thankfully, Intel has been aware of this vulnerability for quite some time and has developed an update that should patch the vulnerability. The update is available through most chipset vendors.
Applying this fix requires users to apply a BIOS update to impacted devices. However, if the thought of flashing hundreds or thousands of chipsets doesn’t sound like your idea of a good time, I don’t blame you. Thankfully, whenever there’s a task you don’t want to do, there’s usually a tool that will do it for you. In this case, that’s SmartDeploy.
SmartDeploy, the powerful agent-based imaging solution, has the ability to deploy drivers and firmware (called Platform Packs) to managed devices. SmartDeploy has been working hard updating their Platform Packs to include the latest Intel Downfall microcode update. Check out our guide on how to deploy drivers and firmware with SmartDeploy. If you’re not already a SmartDeploy customer, no worries. You can try it out for yourself, absolutely free.
Mitigation performance impact
Intel has confirmed that there could be a significant performance impact on systems after applying the updated firmware. While I always recommend testing updates before distributing them, I’d say it’s extra important in this situation.
According to Intel:
“Some datacenter and high-performance computing applications, such as machine learning (ML) libraries, numerical libraries, graphic design and rendering software, and certain scientific applications, may see significant performance impact from the GDS microcode mitigation.”
It’s difficult to know how much the Downfall update will impact your systems, so ensure you thoroughly test a subset of devices that represent your larger network. In certain situations, it may be beneficial to postpone this update, especially if it drastically reduces system performance. While security is always critical, there are situations where the risk is acceptable.





