With cybersecurity risks on the rise, securing your managed endpoints is more critical than ever. And even though remote machines add a layer of complexity to your cybersecurity strategy, keeping your users and devices happy becomes a proverbial piece of cake with the right tools.
I can neither confirm nor deny that I am writing this article from home … in my sweats … while watching Is It Cake?.
Remote device complexities
Managing and securing remote devices has traditionally been more difficult than administering on-prem devices. Some facets of cybersecurity, such as updating antivirus definition files, could be done over the internet. Other security measures, such as patch management and reporting, often required users to connect to their business VPNs to gain device visibility. But as more services became cloud based, remote users had fewer reasons to use their VPNs, leaving sysadmins scrambling for a solution to secure their growing fleet of remote machines.
1. Use an agent-based solution
As remote device VPN usage decreases, so does the effectiveness of on-prem device management solutions. While it’s not impossible to secure remote devices with an on-prem solution, it’s becoming increasingly more difficult to monitor them — which doesn’t match my “I work in sweatpants” lifestyle. As they say, modern problems require modern solutions.
Agent-based solutions, such as PDQ Connect, allow you to secure your remote computers wherever they’re located. With an agent-based solution, you can track inventory, monitor their status, deploy packages, patch vulnerabilities, and build reports for devices worldwide. The only requirement is an active internet connection.
If you’re struggling to manage your remote computers, PDQ Connect is here to help. Sign up for a free trial of PDQ Connect to see how this best-in-class remote device management solution can improve your security posture.
2. Maintain up-to-date information
Accurate information plays a vital role in cybersecurity. It provides visibility into your computer’s security strengths and weaknesses and ultimately leads to decisive action. Readily available, up-to-date information helps you quickly identify machines exposed to exploits and vulnerabilities.
PDQ Connect offers a couple of different methods to ensure your essential data is readily available: groups and reports.
3. Organize devices into groups
Groups in PDQ Connect enable you to organize devices into logical containers. With groups, sysadmins can rapidly determine the status of their organization’s endpoints and use those groups as deployment targets.
You can build groups as static or dynamic collections of objects.
Static groups
Static groups are user-built persistent collections that don’t change unless org admins manually modify them.
Static groups are a great way to organize computers into persistent collections. For example, you can create a static pilot group comprising workstations that are part of your pilot deployment program. Another common use case is to group computers by department using static groups.
How to build static groups in PDQ Connect
Static groups are incredibly quick and easy to create in PDQ Connect.
In PDQ Connect, select the Devices tab.
Click Create group.
Enter a name for the group, then click the Type drop-down menu, and click Static.
Select the devices to add to the group, then click the right arrow button to add them.
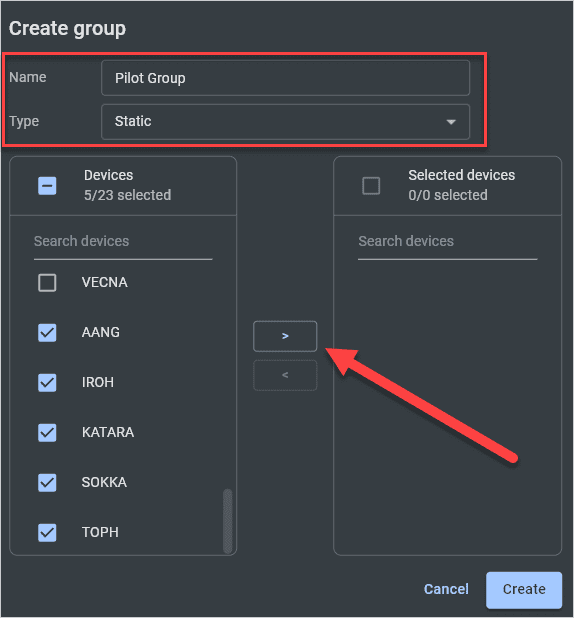
Click Create when finished.
Dynamic groups
Dynamic groups are collections of devices defined by a set of filter rules. As the name suggests, dynamic group memberships are constantly changing. If a computer satisfies the dynamic groups filter rules, it’s added to the group. The computer is removed from the group when it no longer meets the filter rules.
While static groups are maintained manually, dynamic groups automatically reflect changes to your remote computers. There are many use cases for dynamic groups. A couple of common scenarios are to monitor devices that are missing software or running out-of-date software.
PDQ Connect comes with dozens of prebuilt dynamic collections designed to track which computers have old, possibly vulnerable software installed and which have the latest versions installed. There are also several dynamic collections to track important OS data.
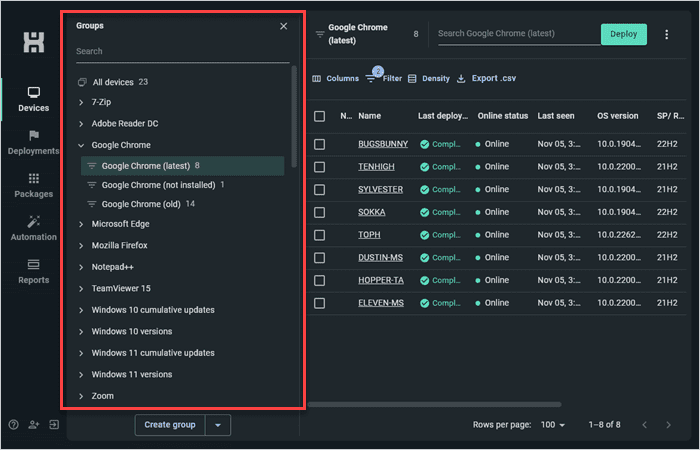
To ensure dynamic collections meet the needs of each unique organization, Connect gives you all the tools necessary to build your own custom dynamic collections.
How to create dynamic groups in PDQ Connect
Building dynamic groups is quite a bit different than building static groups. Instead of assigning devices to a group, you create filter rules determining which devices should be group members.
In the Devices tab of PDQ Connect, click Create group.
Name the group, click the Type drop-down arrow, and click Dynamic.
Enter your filter rules. In this example, I’ll filter for devices with Google Slides installed using: Software | Name | contains | slides.
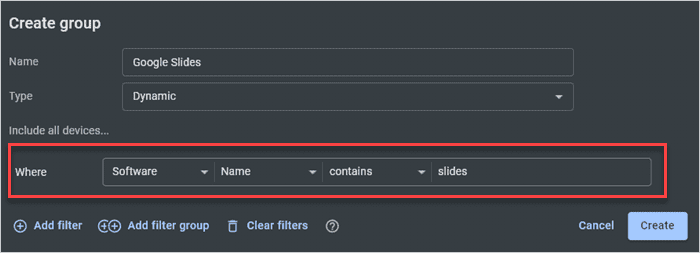
When you finish adding your filters, click Create.
Any devices that match your filter rules are automatically added to the dynamic group.
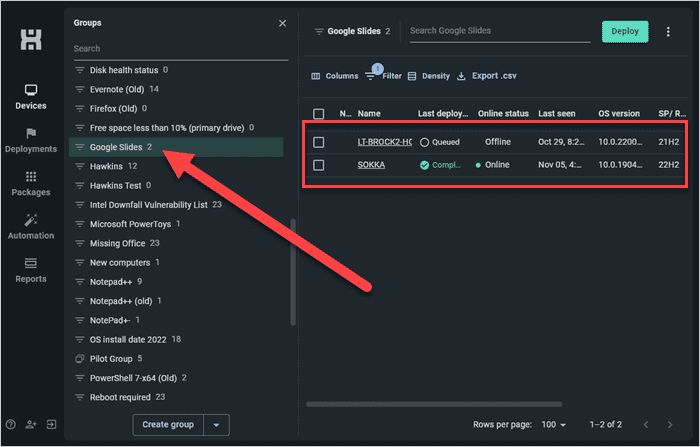
4. Use reports to drive your security strategy
While groups are great at providing rapid insights into your remote machines, reports allow you to easily aggregate your environment data and tailor it to your needs, driving your remote security strategy. Reports also give you the flexibility to export your data and integrate it with other systems. Bonus feature: Reports tend to make upper management really happy, which gets them off your back for a while. Win-win.
How to create reports in PDQ Connect
I’ve yet to meet someone who listed generating reports on their “favorite things to do” list. However, PDQ Connect drastically simplifies the process. Pretty much anyone at any skill level can quickly create reports in PDQ Connect.
Let’s work through the process of creating a software report.
In PDQ Connect, click the Reports tab.
Click Create report.
Add a name.
Click Select columns.
Click the drop-down menu, then select Software.
Select Software: Name, Software: Version, Software: Publisher, Software: Install Date, and Device: Name.
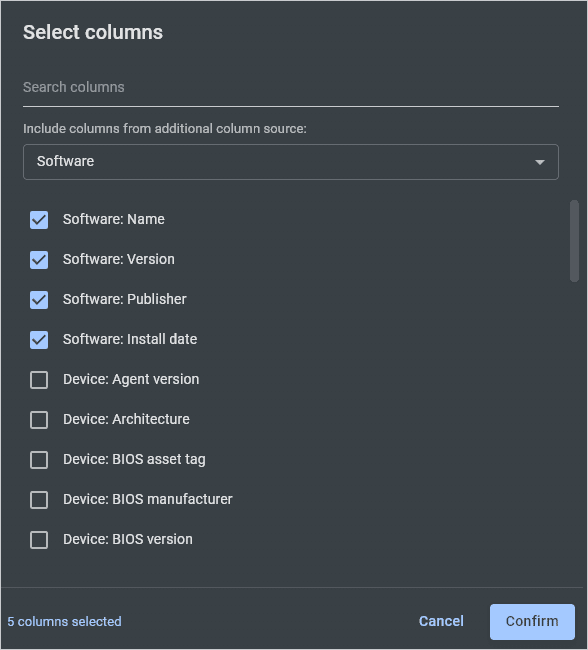
Click Confirm.
Select Group by Software: Name and Group by Software: Version.
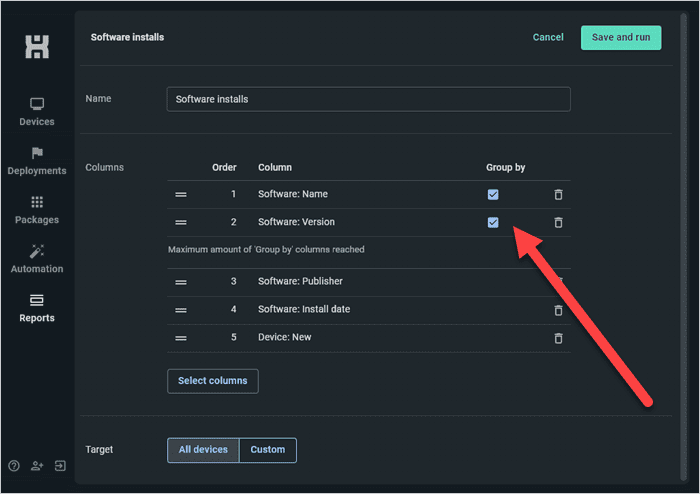
Click Save and run.
The finished product is an easy-to-navigate report with the information you need to secure your remote devices.
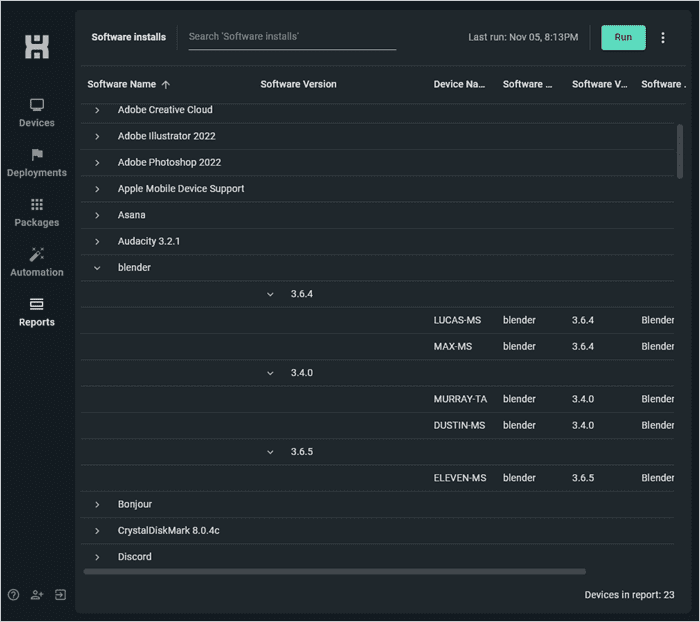
5. Patch remote devices with PDQ Connect
Patch management has been a thorn in the side of sysadmins since the invention of the update, but it’s one of the most essential components of cybersecurity. Patching on-prem devices is challenging enough, but remote devices took this to a whole new level of difficulty. Many IT professionals resorted to turning on automatic updates and then praying for the best. While I feel your pain, this is not the way.
PDQ Connect makes the impossible possible. With the steady stream of up-to-date information gathered by Connect, sysadmins can streamline the patch management process and rapidly distribute updates to remote devices wherever they are. With the help of automation, sysadmins can create an automated process to ensure devices regularly receive critical patches on a schedule that works for them and their users.
How to deploy packages and automate the deployment process
If you’ve ever deployed patches with SCCM or Intune, you can understand how unnecessarily complicated the process can be. PDQ Connect takes the opposite approach and radically simplifies patch management because even IT professionals deserve a little simplicity in their lives. For example, here’s how easy it is to patch devices with an old version of Google Chrome using the built-in Google Chrome group and package.
In PDQ Connect, click Packages.
Locate and select the Google Chrome Enterprise package.
Click Deploy.
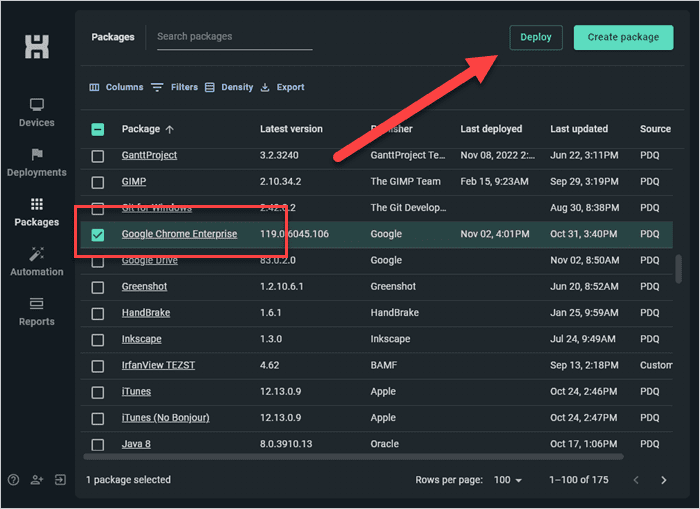
In the Search devices and groups field, enter google then select the Google Chrome (old) group.
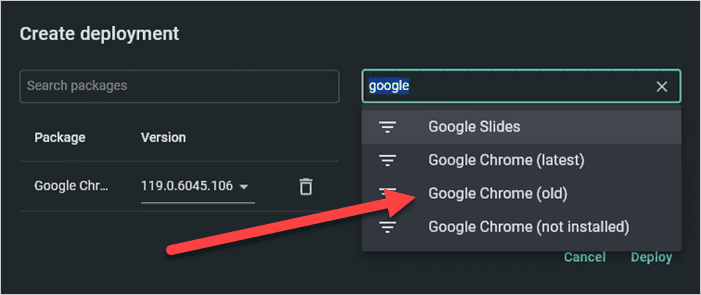
Click Deploy to begin the deployment.
That’s it. That’s the whole process. Select the package, select the targets, and click deploy. While this example used a prebuilt package and a prebuilt group, you can easily create your own custom packages and groups.
Lastly, I highly recommend automating as much of the patch management process as possible. And no, it’s not because I’m lazy … okay, it’s partly because I’m lazy. But it’s also because automation is efficient and reliable.
Here’s how to set up an automation in PDQ Connect.
Click the Automation tab.
Click Create Automation.
Enter a name for the automation.
Select the package from the Packages field.
Select Recurring.
Enter the start date and time.
Select your interval. In this example, I elected to have the automation repeat weekly on Wednesdays.
Select the targets or groups.
Review your settings, then click Save to save your automation.

With a minute’s worth of work, I just automated all my Google Chrome deployments. Who knew securing remote devices could be this easy?
Remote security: This is the way
Securing remote machines can be a daunting task, quickly overwhelming IT professionals. But it doesn’t have to be. PDQ Connect gives you everything you need (minus the sweatpants) to track and secure your remote endpoints. And like icing on the cake, PDQ Detect sweetens your remote device security with actionable, contextualized vulnerability information and clear remediation steps.
The only question remaining is whether or not this is an actual article, or Is It Cake? I may have a problem.











