We don’t live in a perfect world, and we don’t manage perfect network environments. The truth is, most sysadmins deal with missing devices, stale data, and a DNS environment that generally just doesn’t like them for some reason. If you find yourself struggling to keep up with your growing fleet of devices, don’t worry. You can drastically improve your situation with a few configuration changes and the right tools. Here are five tips to help you simplify network inventory management.
1. Organize and continually maintain Active Directory
Active Directory (AD) is the heart of most network environments. AD provides essential administrative functions, such as managing authentication requests, delegating access to network resources, and storing and organizing information about network resources and objects.
When properly structured and maintained, AD can provide exceptional administrative control. However, AD can quickly become bloated with stale objects, especially in rapidly growing organizations. Moreover, leveraging certain administrative tools, such as group policy, can be more difficult if AD isn’t properly structured.
Tips to help organize and manage your AD environment:
Disable accounts immediately upon a user’s departure from the organization. Some organizations leave accounts disabled indefinitely, while others delete disabled accounts after a given number of days. Discuss with your team and consider a policy that works best for your environment.
Move disabled accounts into a designated disabled accounts organizational unit (OU) to keep production OUs clean.
PowerShell is your friend. You can use it to automate many tasks, such as moving and deleting accounts in AD. If you don’t want your day filled with manual tasks, PowerShell is the way to go.
Separate OUs containing user objects, computer objects, and security groups.
Organize OUs based on location and departments. Properly structuring OUs in Active Directory can drastically simplify Group Policy management.
It’s important to remember these tips are things to consider but won’t work for all environments. Develop a cohesive strategy that’s best for your network, devices, and users. Keep what works and change what doesn’t.
2. Populate Active Directory with useful information
Active Directory isn’t just great for accumulating and organizing objects. It also excels at storing object data.
Attributes in Active Directory are bits of information that define the properties of AD objects. Sysadmins can leverage hundreds of attributes defined in AD to extend AD’s functionality. This information can be extremely beneficial for identifying, categorizing, and reporting on devices.
Many object attributes are populated and regularly updated automatically in AD, including:
cn (Common Name)
distinguishedName
lastLogon
logonCount
objectSid
operatingSystem
operatingSystemVersion
whenCreated
However, admins can also take advantage of tons of attributes that AD doesn’t automatically utilize, such as:
comment
company
department
description
location
serialNumber
Now, all that’s left to do is manually input this information for each computer object in your domain … Okay, put the pitchforks down; I’m kidding. Besides, we’re far too lazy and far too smart for that. Instead, we can utilize PowerShell and a CSV file to do the heavy lifting. Here’s an example CSV file containing information I want to add to some of my computer objects.
sAMAccountName,location,department,serialNumber
HEIMDALL$,Asgard,Transportation,123888463
SIF$,Mars,Public Relations,88463389
THOR$,Earth,Security,1588946237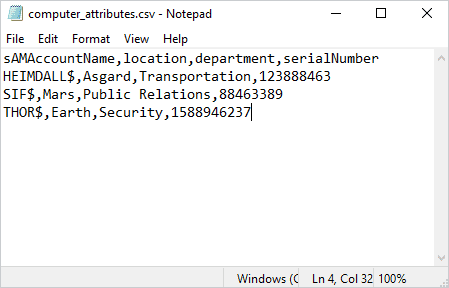
This CSV file contains the location, department, and serial number data for three computers. PowerShell can easily import this data in Active Directory for us with a simple script:
$Computers = Import-Csv -Path C:\CSV\computer_attributes.csv
ForEach ($Computer In $Computers)
{
$sAMAccountName = $Computer.sAMAccountName
$location = $Computer.location
$department = $Computer.department
$serialNumber = $Computer.serialNumber
Set-ADComputer -Identity $sAMAccountName -Location $location -Replace @{department=$department;serialNumber=$serialNumber}
}
All you need to do now is upscale this example to meet your needs and populate your Active Directory with all sorts of helpful information.
3. Get DNS in shape
I love the old domain name system (DNS) haiku that has been floating around the internet for several years now:
It’s not DNS
There’s no way it’s DNS
It was DNS
— SSBroski of Reddit
This haiku faithfully summarizes DNS and also seems to accurately depict the quintessential routine of a sysadmin.
DNS is the hidden superhero lurking in the shadows making all our lives exponentially better while receiving little credit. However, while DNS is largely to thank for connecting us to our digital destinations, it’s also notorious for being the root of many sysadmin-related conundrums.
DNS translates human-rememberable device and domain names to IP addresses. It allows me to connect to my server LordOfThePings using its super great name, which is easy to remember, rather than an IP address like 10.10.218.242.
When DNS works, it’s incredibly valuable. When it doesn’t work, it’s the source of many sysadmin tears. Thankfully, getting DNS in shape is pretty straightforward. Check out our DNS guide, specifically the section about fixing common DNS issues, to learn how to configure scavenging properly and enable dynamic DNS updates on your DHCP server.
4. Group devices to help with patching
Organizing and maintaining a large fleet of devices is no easy task. Even more challenging is ensuring all those devices get adequately cared for and regularly updated to help defend against cyberattacks.
Digital threats continue to rise year after year. There are several contributing factors to this unfortunate statistic. The skill requirement for cybercriminals is lowered all the time. The cost of data is rising, meaning successful attacks are more lucrative than ever. And organizations are continually adding to their fleet of networked devices, increasing their attack vector footprint.
As cyberattacks increase, it becomes significantly more important to ensure all managed network devices are regularly updated with security patches. Unfortunately, updates don’t have a perfect track record of being bug free. To ensure devices get updated on time and minimize distributing patches that could negatively impact your environment, organize your devices into patching groups.
Devices should be divided into a minimum of three categories, a pilot group, a production group, and a critical group. If you need more groups to organize your devices, go nuts! The sky’s the limit.
5. Use a network inventory management system
At some point, your fleet of devices will grow beyond your capability to administer without some additional help. A nice warm body to help manage your devices and provide the occasional hug when DNS is acting up sure would be nice, but that’s a luxury many sysadmins don’t get. You can compensate for the lack of additional personnel by investing in a proper inventory management solution, like PDQ Inventory.
PDQ Inventory comes ready to identify, organize, and simplify your device management right out of the box. From the moment you sync it with Active Directory, PDQ inventory gathers highly detailed information from your endpoints and presents that information in a way that is easy to digest.
Want to know what devices have the latest security updates installed? How about which machines have old versions of VLC Media Player installed? Want to see what devices are currently online? What about identifying computers with less than 4 GB of memory? PDQ Inventory makes all this information available immediately. PDQ Inventory can even help you identify potentially vulnerable applications on your network.
There a three key features of PDQ Inventory that separate it from the majority of inventory management systems on the market:
PDQ Inventory is unbelievably simple to use. Install PDQ Inventory, sync it with Active Directory, then sit back and relax. You can be up and running with PDQ Inventory in about five minutes.
By default, PDQ Inventory identifies and categorizes about 99% of the information you’ll ever need from a device, including collections for popular applications, hardware statistics, OS information, and more.
PDQ Inventory is highly customizable and extensible, meaning you can easily collect, categorize, and report on the other 1% of information that Inventory doesn’t collect by default with the help of a built-in WMI and PowerShell Scanner.
Don’t put off your inventory management overhaul
If you find yourself drowning in an ever-deepening sea of devices, it’s not too late. These tips, some TLC, and the right tools can help you regain control of your network.
If you’re looking for an inventory management solution that provides all the power without all the complexity, PDQ Inventory may be the tool for you. Try it out for yourself with a 14-day free trial.