Architecture overview
Introduction to PDQ Deploy & Inventory
PDQ Deploy & Inventory is a desktop/server-based device management tool. IT professionals and sysadmins use PDQ Deploy & Inventory to manage the devices in their organization. IT professionals perform actions like scanning endpoints for device information, organizing devices into collections, creating reports, updating software, and running scripts on devices — all through their local network.
Product architecture
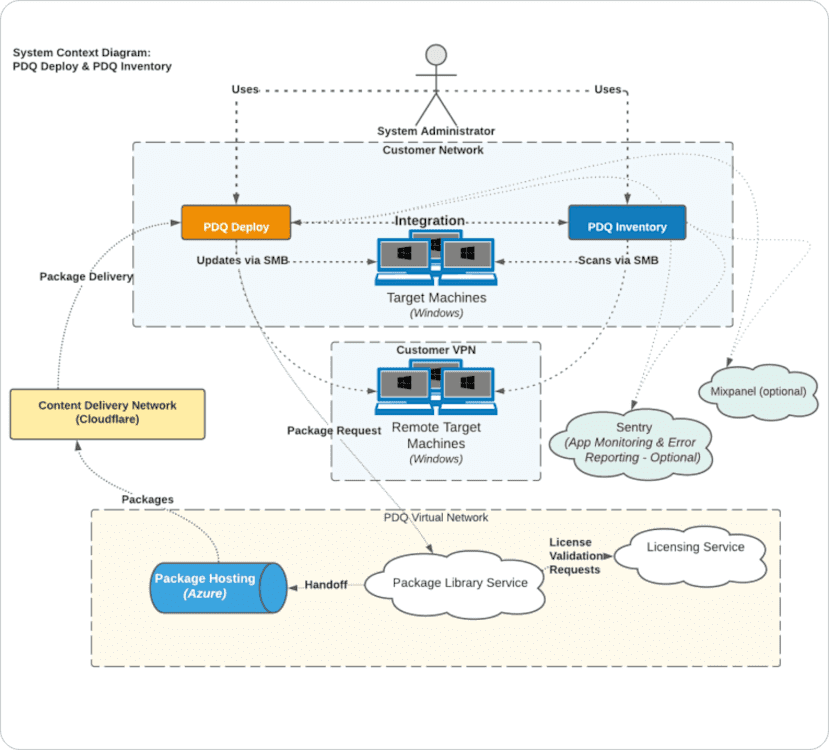
To remotely manage devices, PDQ Deploy & Inventory uses an agentless, client/server model to interact with endpoints. Standard Windows authentication is used to create a temporary service on the client in order to deploy software or perform an inventory scan. Once completed, the temporary files and service are deleted.
PDQ Deploy & Inventory Admin Console
Administrators use the PDQ Deploy & Inventory Admin Console to configure computers, create packages, and update computers. The Admin Console is part of the PDQ Deploy and Inventory Applications.
The console is where administrators can see information about the devices they manage, as well as create and observe package deployments. When packages are deployed to devices, the setup and configuration options of that deployment are sent over SMB to devices as described in the product architecture.
Data security
Encryption
At rest:
PDQ encrypts all sensitive information (passwords) stored in the PDQ databases that are stored internally on your organization’s network. We use industry-standard AES encryption with three separate keys to keep your data safe. One key is built into the application, one is stored in the database, and the third is stored in the registry. These last two keys are generated when the application is installed and are unique to your system. The rest of the data is stored decrypted in the local SQLite Databases.
In transit:
The PDQ server uses an agentless, client/server model to interact with endpoints. Standard Windows authentication is used to create a temporary service on the client in order to deploy software or perform an inventory scan. Once completed, the temporary files and service are deleted.
External traffic
PDQ Deploy and Inventory regularly access the internet to update the Package Library, Collection Library, Tools Library, and System Variables (used in collections). Additionally, PDQ products check for program updates, license expiration information, and general information notifications from PDQ.com (webcast notices, beta notices, etc.). This is all done via HTTPS.
Data isolation
All data within the PDQ Deploy & Inventory databases is locally stored on your network. You can change the location of the database in the preferences.
Data backups
Database backup is controlled by the settings you choose in preferences; the location and frequency are up to the end user.
Support
Our support staff may ask you to submit your databases so we can get more information to help fix your problem. When you submit your databases, these include PDQ databases, log files, and errors in the Windows event log, and PDQ Server configuration information.
We don't have any access to customer databases, unless you manually submit them as part of a support ticket. When we receive these databases, we do not have access to the customer's stored passwords. We do have access to hardware and software inventory information that can include computer names, IP and MAC addresses, and logged-on usernames.
We don't have a formal retention policy, because sometimes we close a ticket and the customer needs additional support and re-opens the case. It's more based on clearing space for new ticket uploads, which typically ends up being around three to six months. If a customer specifically requests the deletion of their data, the support engineer immediately honors that request.
Identity and authentication
Identity and authentication overview
PDQ Deploy & Inventory are desktop/server applications and thus do not have authentication currently; all access is controlled by existing Windows authentication.
Password requirements
Password requirements are dictated by the organization, as Deploy and Inventory uses existing credentials to authenticate with machines.
Operational security
Vulnerability prevention
PDQ has established a Vulnerability Monitoring and Scanning Program designed to identify, quantify, and prioritize internal and external vulnerabilities in systems and hosted applications at least weekly (or more randomly). PDQ also identifies and implements code analysis tools in the organization’s development pipeline to regularly scan both static and dynamic codebases to check for vulnerabilities. Processes ensure that the scope of any vulnerability is defined and documented before initiating a vulnerability assessment.
PDQ also ensures that all findings from vulnerability scans are analyzed and documented weekly and remediated in accordance with the organization's risk tolerance. PDQ shares information obtained from the vulnerability monitoring process and control assessments with key stakeholders to help eliminate similar vulnerabilities in other systems.
Other security topics
Third-party vendors
PDQ Deploy & Inventory utilize a handful of services required to provide product functionality. These third-party vendors process data for PDQ:
Provider | Service | Notes |
|---|---|---|
Mixpanel | Usage tracking | Used for tracking feature usage in PDQ Deploy & Inventory. (optional) |
Sentry | Logging | Used for identifying and logging bugs or other product issues. (optional) |
Security audits
PDQ performs annual human-based and weekly automated penetration tests to identify vulnerabilities that could be exploited to gain access to its production environment. PDQ ensures that in-scope assets are documented before initiating of any penetration test. PDQ’s internal Deploy & Inventory team has committed to an internal SLA to remediate issues found by these tests.
Additionally, PDQ has engaged a third-party bug bounty program that pays out for non-publicly disclosed vulnerabilities.
Certifications
PDQ takes security seriously and realizes the value of independently audited security certifications. We are SOC 2 compliant and will continue to undergo routine audits for updated reports.
Package Library
PDQ Deploy & Inventory offer an optional feature called the Package Library. This feature allows organizations to pull packages for popular applications from PDQ — without having to manage the packages themselves. For example, PDQ keeps the latest version of Chrome available in the Package Library, making it easy for organizations to deploy the latest browser version to target devices.
This is an optional feature included with PDQ Deploy & Inventory. Organizations can choose not to use this feature and instead manually create packages.
Package creation process
To create a software package, a proprietary PDQ system periodically scans software providers for new updates and downloads them to the PDQ package repository. As available, PDQ submits the hashes for these products to a third-party site for reputation analysis, which leverages multiple antivirus engines.
All packages are built using a secured virtual machine that is dedicated to the creation of packages. Once a package is built, it is manually tested with a group of virtual machines, each with a different version of Windows installed. Each machine is then analyzed to ensure a successful deployment. Furthermore, each package is tested on an additional device that utilizes both antivirus signatures and behavior-based scanning to ensure each package is secure and virus free.
This process is manually verified by a secondary engineer for quality assurance. At no point can a single engineer build and publish into the library. Once the package passes secondary validation, the package is uploaded to the Package Library and made available in PDQ products.
The packages available in the PDQ Package Library can be found here.
Custom packages
Customers can optionally create their own packages and upload their own software to PDQ Deploy & Inventory. PDQ does not share or in any way make available, custom packages created by one customer with other PDQ Deploy & Inventory customers. The customer is responsible for ensuring the packages they create are safe.
