VULNERABILITY MANAGEMENT SOFTWARE
Detect, prioritize, and patch vulnerabilities
Mitigate vulnerabilities before threat actors exploit them, and skip the whole sweating-through-your-shirt-while-trying-not-to-cry thing.

Stay ahead of threats
Save time, cut through the noise, and secure your environment with PDQ Connect.
Know what’s at risk — and how to protect it
Identify and understand vulnerabilities across your environment with real-time visibility and context-rich data.

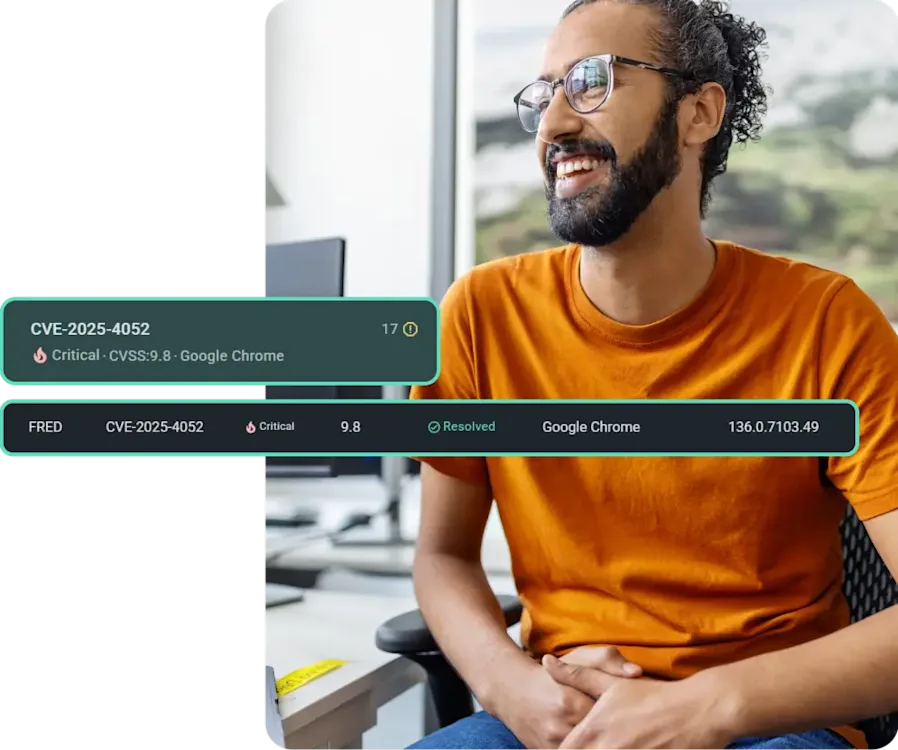
Vulnerability scanner
Scan for potential vulnerabilities in your operating systems and software. Or manually initiate a scan to verify you resolved issues without introducing new CVEs.
Asset discovery
Maintain full visibility with an up-to-date inventory of hardware and software. Keep track of installed versions, deployments, connected drives, assets, and more.
CVE information
Gather insights into vulnerabilities, including a PDQ risk score that factors in CVSS, business impact, access levels, and exploitability, all to support smarter CVE prioritization.

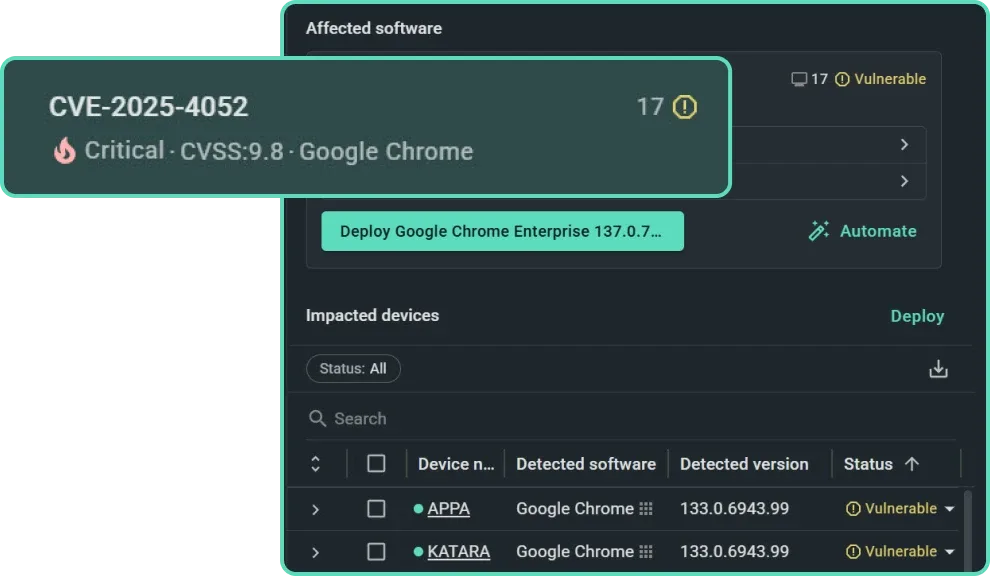
Remediate fast, then rest easy
Resolve vulnerabilities quickly with automated patching workflows and targeted CVE remediation.
Prioritize automatically
Automatic CVE prioritization puts high-risk vulnerabilities front and center to cut through the noise.
Patch immediately
Connect suggests prebuilt packages if they'll resolve a detected vulnerability — simply click for fast CVE remediation.
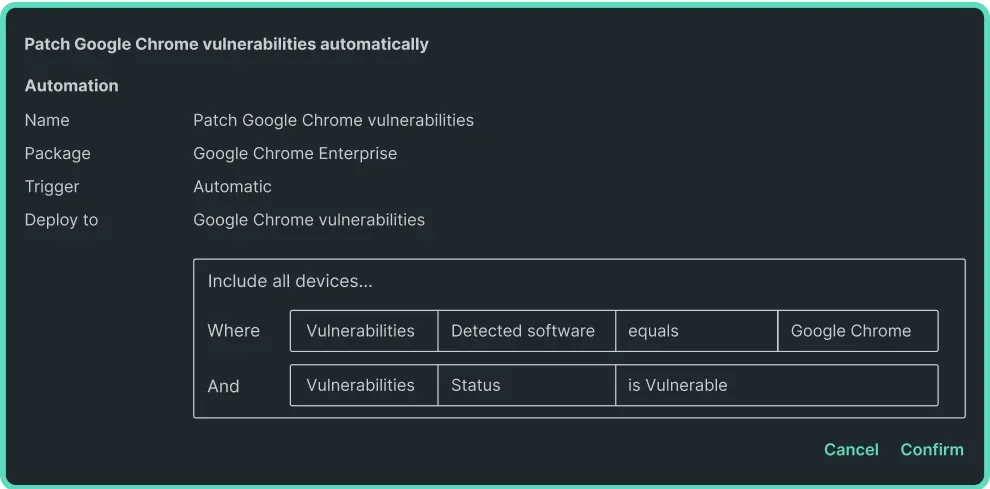
Automate future patches
For any prebuilt package Connect maintains, the latest version deploys the moment a new CVE is detected.
Reports that speak for themselves
Create reports that make your job easier — and your results undeniable.
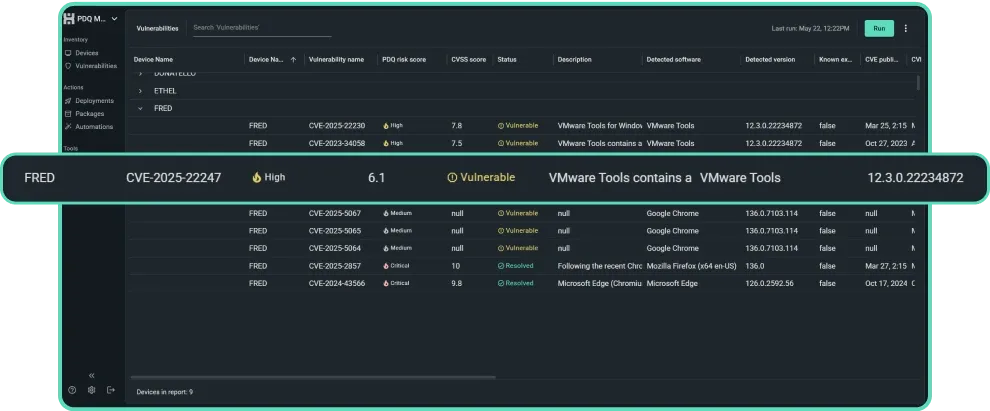

Prebuilt reports
Get a snapshot of vulnerabilities, security risk scores, status, and more. Nothing says “Give me a promotion” like handing your boss a thick stack of vulnerability scan reports.
Automatic reporting
Create custom reports and schedule any report to update and email out to chosen contacts on a set schedule. Enjoy having an easy button for collaboration.
Deployment history
See exactly what was deployed, when, and to which machines. Detailed logs and real-time accuracy take the mystery out of IT — even across remote endpoints.
“When you resolve a vulnerability in Connect, you can scan the device again, and it confirms — yep, job done."
David Elliott, hsy autoparts


4.8 of 5 stars on Capterra
95% likely to recommend to others
4.9 of 5 stars on G2
Try PDQ Connect to find and fix vulnerabilities fast.
FAQs
What is a vulnerability?
A vulnerability is a weakness or error in software, hardware, a network, or a system. Vulnerabilities pose a threat to businesses because threat actors often leverage them to launch cyberattacks. Some of the most common types of vulnerabilities include phishing, zero days, remote code execution, unpatched software, insider threats, security misconfigurations, and weak or stolen user credentials.
What is vulnerability management?
Vulnerability management is the process of identifying, remediating, and monitoring vulnerabilities that impact your environment. Oftentimes, IT teams rely on vulnerability management software to automate parts of the process (such as vulnerability scanning) that would otherwise be unmanageable for small and midsized teams.
What is a vulnerability management process?
The vulnerability management process has six main steps: inventorying assets and then scanning, assessing, prioritizing, remediating, and monitoring vulnerabilities. To enhance your vulnerability management program, you might consider conducting cybersecurity tests, assessing organizational needs and risks, building a cross-functional team, standardizing processes and workflows, and automating vulnerability management tasks when possible.
What are vulnerability management best practices?
Start with regular scans and prompt patching, especially for high-risk vulnerabilities. Prioritize fixes based on impact, automate updates where possible, and keep detailed records for compliance. Tools like PDQ Connect help streamline patch management, while automated software updates reduce manual effort. A proactive, well-documented strategy keeps your systems secure and your team one step ahead.
What are the benefits of vulnerability management?
Vulnerability management enhances security and reduces risk — but the benefits extend far beyond patching. A strong vulnerability management strategy enhances security, reduces risk exposure, improves efficiency, and provides greater visibility into your environment. It also supports regulatory compliance, delivers strong ROI, and helps IT teams respond quickly without burning out. With features like automated deployments and patch scheduling, it’s easier to stay ahead of threats before they turn into problems.
How does vulnerability management relate to patch management, asset inventory, and compliance?
Vulnerability management links together patching, asset inventory, and compliance. It starts with knowing which assets you have — because you can’t secure what you can’t see. A solid IT asset management solution helps you track devices and software, making it easier to identify and prioritize vulnerabilities. Patch management then closes those gaps, while detailed logging and remediation support compliance efforts. Together, they form a cohesive strategy that keeps your systems secure and auditors happy.
How often should you scan for vulnerabilities?
You should scan weekly for vulnerabilities or after any major system changes, such as installing new software or applying updates. The more dynamic your environment, the more frequent your scans should be. Avoid turning scanning into a quarterly fire drill — regular scans keep risk exposure low. For help staying proactive, check out our guide on how to prioritize vulnerabilities.
How do you choose the right vulnerability management software?
Choosing the right vulnerability management software starts with understanding your environment, goals, and available resources. Look for solutions that offer asset discovery, broad scan coverage, contextualized prioritization, and built-in remediation tools. Ease of use, scalability, reporting features, and vendor reputation also matter.
A solid platform should align with your patching and inventory workflows. Tools like PDQ Connect pair real-time visibility with automation, making it easier to prioritize and fix issues as part of your proactive cybersecurity strategy.
How does PDQ help identify software vulnerabilities?
PDQ helps identify IT vulnerabilities by giving you real-time insights into what's installed across your fleet — and what's vulnerable. With tools like PDQ Connect's vulnerability scanner, you can quickly spot outdated or unpatched software and take action before it becomes a liability. It’s a faster, smarter way to stay ahead of potential exploits — without digging through every machine manually.
Can PDQ show which devices are missing critical patches?
Yes, PDQ can show which devices are missing critical patches. PDQ Connect gives you clear visibility into which devices are missing critical patches — so you can act fast and stay ahead of vulnerabilities. With PDQ’s patch management software, you can automate scans, track patch status across your fleet, and prioritize updates based on severity. No guesswork. Just clarity.
Does PDQ use CVEs or vulnerability scoring to flag risks?
Yes, PDQ uses CVEs (Common Vulnerabilities and Exposures) and industry-standard vulnerability scoring to help you flag and prioritize risks effectively. This makes it easier to understand which issues in your unique environment need immediate attention. For a closer look at how these insights are built into PDQ Connect, check out this article on PDQ Connect’s latest vulnerability management features.
How does PDQ support patching vulnerabilities once they’re detected?
Once vulnerabilities are detected, PDQ makes patching straightforward. With PDQ Connect, you can automate patch deployments across remote devices, ensuring updates are applied as soon as they're available. Even better, PDQ Connect automatically suggests prebuilt packages if they’ll resolve a detected vulnerability. All you have to do is click to deploy fixes. Real-time visibility helps you track which machines need attention, while customizable scheduling lets you patch without disrupting users. Patching vulnerabilities with PDQ is fast, flexible, and built to keep your systems secure with minimal manual effort.
Can I automate software patching in response to detected vulnerabilities in PDQ?
Yes, PDQ Connect lets you automate software patching based on detected vulnerabilities — so you’re not stuck chasing updates manually. You can create schedules, set conditions, and ensure critical patches are applied as soon as they’re available. PDQ Connect’s automation features are designed to keep your systems secure with less hands-on work.
