Phishing is a social engineering attack that mimics an authentic communication to trick a user into performing the desired action. Most phishing attempts use fraudulent emails to lure a potential victim into opening a malicious link or attachment, provide banking information, or share login credentials. A threat actor’s ultimate goal is to steal money, acquire confidential information, or install malware.
Like all social engineering attacks, phishing relies on psychological manipulation. Attempts frequently leverage powerful emotions, such as urgency, greed, fear, and curiosity, to motivate victims to act quickly. Since the communication may appear to be from a legitimate company, users often take action before they even have time to question it.
Phishing is inherently deceptive, but that doesn’t mean your company will undoubtedly succumb to a compromise. By understanding phishing, knowing what to look for, and implementing appropriate prevention strategies, you can help keep your business safe (and annoy the heck out of cybercriminals.)

What are common types of phishing?
Common types of phishing attacks include email phishing, angler phishing, vishing, smishing, spear phishing, and whaling. Phishing methods often overlap, so the same attack may fall into several categories.
Common phishing mediums
Email phishing
As the most traditional method, email phishing is what garnered the approach widespread attention. The target receives an email that appears to be from a known party or trusted organization. That phishing email may contain a malicious link, an attachment that installs malware, or a request for sensitive information.
Example: In 2014, Sony Pictures experienced email phishing attacks attributed to North Korea. The emails mimicked messages from Apple requesting that recipients verify their Apple IDs. Once the attackers gained entry, they stole financial records, emails, and copies of films before erasing the hard drives using malware.
Angler phishing
Angler phishing uses social media accounts that appear to belong to legitimate organizations. Cybercriminals use these fraudulent accounts to reach out to customers. In many cases, they find their targets by looking at who posted public complaints or questions. The attackers may post a malicious link to supposed “support” or request that the customer send their account information via direct message.
Example: One popular angler phishing attempt is the Instagram copyright infringement scam. The threat actor sends a message from an Instagram account that appears legitimate. They claim that the target has infringed on their copyright, and the account will be disabled unless the victim follows a link to appeal. Through this link, the cybercriminal collects the user’s login credentials, then uses them to change the password. Finally, they demand ransom to return the account to its original owner.
Vishing
Vishing refers to voice phishing. This phishing scam relies on deceptive phone calls or voice messages. Scammers may claim to be from a respected company, a bank, or even a law enforcement agency. They might say your account has been compromised or offer computer assistance. However, they’re actually seeking out personal information, such as financial account numbers or login credentials, or aiming to install malware on your computer.
Example: In 2021, reports emerged of hybrid phishing/vishing attacks in which the scammers sent a phishing email impersonating Best Buy’s Geek Squad. The email claimed that the recipient would be reenrolled in an annual protection plan at a cost of over $300. It included a phone number, baiting victims into calling to cancel.
Smishing
Smishing is a text-based social engineering approach. Victims receive a deceptive text message. It may redirect them to a malicious website that triggers a download or contains a form that steals personal information. Alternatively, the message may request that the recipient call “support,” incorporating elements of vishing to acquire personal information.
Example: Many businesses and individuals alike are familiar with fraudulent delivery notifications purportedly from the United States Postal Service. The text messages claim that the recipient must respond via a link, which then asks for personal and/or financial information.

Common phishing methods
Spear phishing
In contrast to broader “spray and pray” attacks, spear phishing targets a specific individual within an organization. Attackers often research the victim to customize the message, making it appear more trustworthy.
Example: In 2016, swindlers stole more than $100 million from Facebook and Google via an elaborate spear phishing campaign. The scammers established a fake business impersonating a legitimate company, Taiwan-based Quanta Computer. They then sent fraudulent invoices to employees within the organizations who regularly did business with Quanta Computer.
Whaling
Whaling is a type of spear phishing attack that goes after higher-ups, such as CEOs. While the targets tend to be savvy about common threat tactics, their high profiles lead to an abundance of publicly available information. Scammers can leverage these personal details to customize a convincing message.
If a high-level employee hands over their credentials, the threat actor can then send messages as that individual. Since employees are usually eager to please those in power, they’re likely to do what the scammer requests, whether that’s providing financial information or handing over trade secrets.
Example: In 2020, Australian-based hedge fund Levitas Capital closed after a successful whaling attack. A scammer sent a fake Zoom invite, which was opened by one of the company’s cofounders. The link installed malicious software that gave the cybercriminals control over the email system. From there, they sent fraudulent invoices. Ultimately, the swindlers only got about $800,000 AUD ($587,000 USD), but the damage to the company’s reputation caused a major client to pull an investment, ultimately sinking the fund.
How can you identify phishing?
Even employees who are highly knowledgeable about phishing techniques may fall for particularly clever scams. However, knowing what to look for can help your team prevent phishing attacks.
Examine hyperlinks carefully
Hover your mouse over any hyperlinked text or button to look at the associated address. The address should match the context of the message. For instance, if an email claims to be about your Spotify account, the link should go to an address on a Spotify domain.
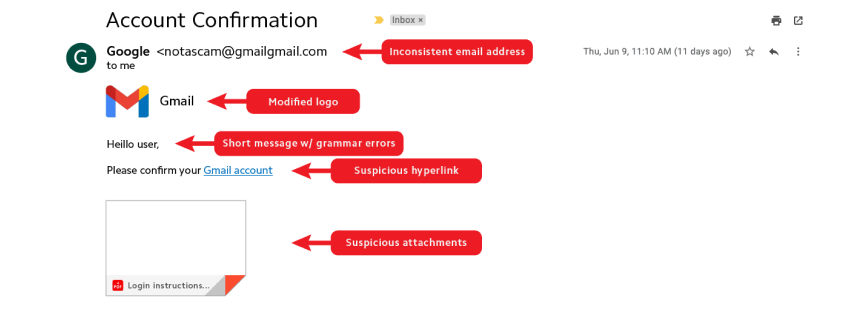
Check for inconsistent email addresses
Just like hyperlinks, you should carefully investigate any email addresses. In many cases, email addresses used in phishing scams have a similar domain to a legitimate company. However, eagle-eyed scam spotters can find issues.
For instance, an email purported to be from Google should come from @google.com rather than @gmail.com. In fact, let’s just assume that most emails sent from reputable companies won’t use a free email account, such as @gmail.com, @hotmail.com, @aol.com, or @yahoo.com.
Look for modified brand logos
While many scammers use a legitimate company’s logo, it’s often slightly modified. If you don’t quite remember what a logo is supposed to look like, go to the official website and compare the two head-to-head.
Notice suspicious attachments or links
Malicious links and attachments are a phisher’s bread and butter. Any time you receive an unexpected attachment, think twice before opening it and look for other signs of deception. Suspicious links can be a little harder to suss out, but using the aforementioned techniques can help.
Consider the content of the email
A phishing email may contain one or more of the following:
Short or image-based emails to evade detection
Typos, grammar issues, and spelling errors
Generic or unfamiliar greetings
Requests for login credentials, billing information, or other sensitive data
Take a hot pause if you notice any of these things within the email. When in doubt, use an established channel to contact the company that supposedly sent the message and confirm its authenticity.

What are the potential consequences of a successful phishing attempt?
Phishing attacks can have far-reaching effects on your business. These may include:
Compromised credentials: Cybercriminals frequently use phishing attacks to get login information and passwords. They can then use this information to access key accounts with sensitive data, like client information, financial records, and proprietary knowledge.
Stolen funds: Many phishing scams are just looking to make a quick buck. They might do this by tricking an employee into sharing bank account information or paying an “invoice.” However, your company may be out even more money since reputational damage can cost you valuable business.
Exposure of personal information: Think of all the data you have in your systems. You may have client information, trade secrets, or other critical details you’d rather keep private. A phishing attack could allow an outsider access to this sensitive information, hitting your information security where it hurts.
Malware: Many phishing attacks install malware, such as ransomware or a keylogger. A hacker can use ransomware to block your access to critical files and demand payment to release them. Meanwhile, a keylogger records each keystroke, which can provide a wealth of information on login credentials, bank accounts, and more.
Reputational damage: Reputation is valuable, accounting for 63% of your company’s market value. A successful phishing attack can reduce confidence in your company, which can, in turn, hurt your bottom line.
How can you prevent and avoid phishing impacting your business?
The same policies and procedures that enhance your overall cybersecurity posture are also valuable for shielding your company against phishing-related losses.
Train employees in security awareness: Even if employees understand what phishing is, they don’t always know how to spot a real attempt. Awareness training with simulated phishing tests can prepare them for the real thing.
Update software: While software updates won’t stop phishing attempts, they can patch vulnerabilities that malware might otherwise exploit. That means if an employee accidentally clicks a malicious link or attachment, the malware might not get a foothold in your system. And since PDQ Deploy and PDQ Inventory make deployment quick and painless, there’s no reason to leave your machines unnecessarily exposed.
Use a spam filter: Spam filters aren’t 100% effective against phishing, but they can weed out some of the more obvious attempts.
Use high-quality security software: Some high-quality security software has anti-phishing features that can detect and contain suspicious emails.
Back up data: If a phishing attack succeeds and your computers are compromised, maintaining a secure backup can get you back in business much more quickly.
Don’t click links or download attachments from unknown sources: Seriously, though. Don’t.
Avoid sharing personal information via email: Especially when finances are involved, try to confirm with the supposed sender via another trusted channel. For instance, if you know their phone number, you might speak to them directly to confirm that they actually sent you the email.
Use multi-factor authentication: Phishing attempts often aim to acquire credentials. Multi-factor authentication adds an extra layer of security (usually a one-time use password from an app, email, or text message) so that scammers can’t access accounts with just a username and password.


