PDQ Inventory: Streamline your systems management
Scan, collect, and organize your on-prem Windows machines so deployments go exactly where you need them to with PDQ Inventory.


The Swiss Army knife of sysadmin tools
Free yourself and your team from pesky, repetitive tasks by unlocking powerful automations so everyone can focus on the important things, like a spirited debate over what to order for lunch.
Efficiently organize your network inventory
Gain immediate, deep visibility into your environment so you can quickly spot and address machines that need attention. 20/20 vision into your environment, and no optometrist appointment necessary.
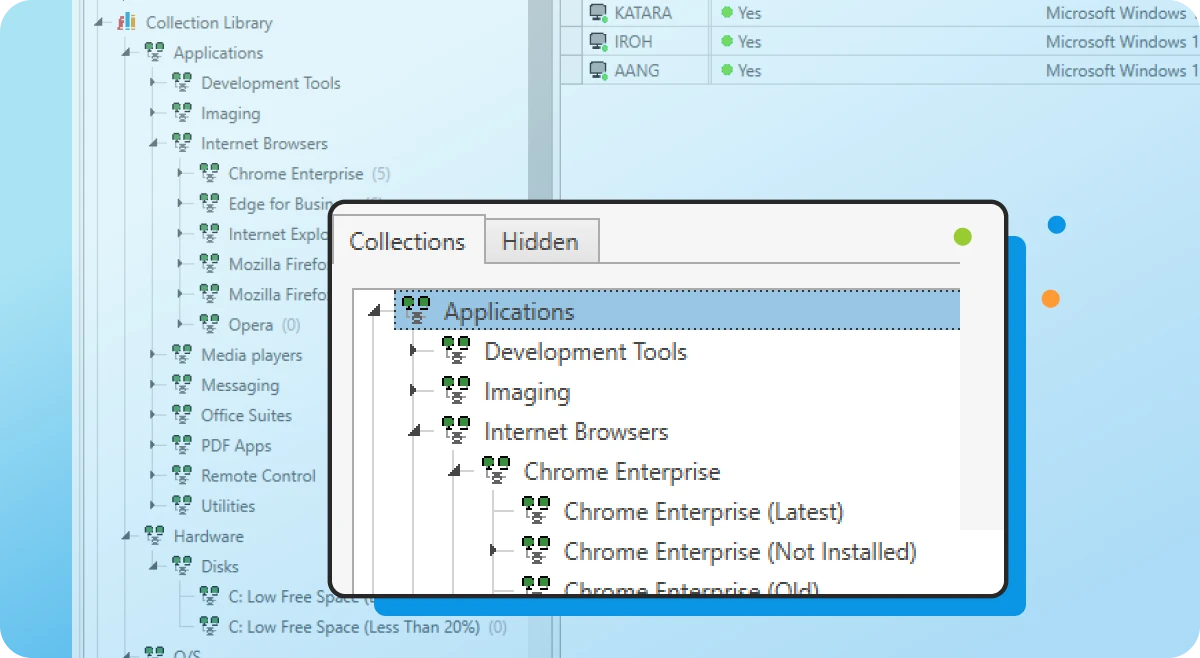

Collection Library
Save time with our prebuilt device groups, which provide a real-time display of which machines have old software versions installed or are low on disk space.
Custom collections
Create collections of devices to meet your specific needs. These groupings can either be static or set to dynamically include new computers that meet your defined criteria.
Auto sync with AD
Enable PDQ Inventory to automatically import computer records from your Active Directory domain for accurate, centralized visibility of your inventory data.
Get centralized, tailored inventory insights
Get specific on what matters most to you and save time in the long run by pulling in additional data and automating repeat tasks. Please let us do more of your work for you, we insist.
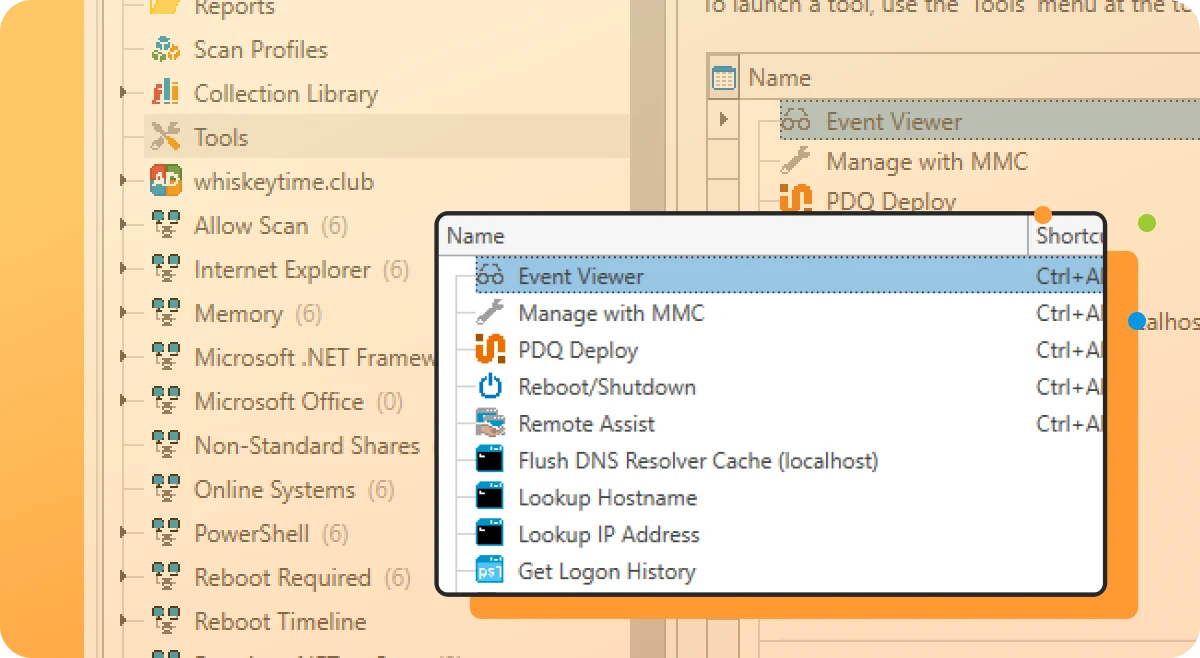

Custom scanners
Bring additional scanned data, like specific registry data or custom script results, into PDQ Inventory for more thorough monitoring and investigation of your environment.
Custom tools
Utilize prebuilt tools for reboots, remote assistance, and Wake-on-LAN, or create and save your own tool for any command that can be run with Windows.
Custom variables
Create and store custom values for repeated use, like the version number of a custom software application, or static fields like a computer’s department.
Integrate inventory workflows
Automate your workflow by leveraging both PDQ Inventory and Deploy together, and efficiently collaborate with teammates to ensure everyone sees what they need, in a pretty damn quick fashion.
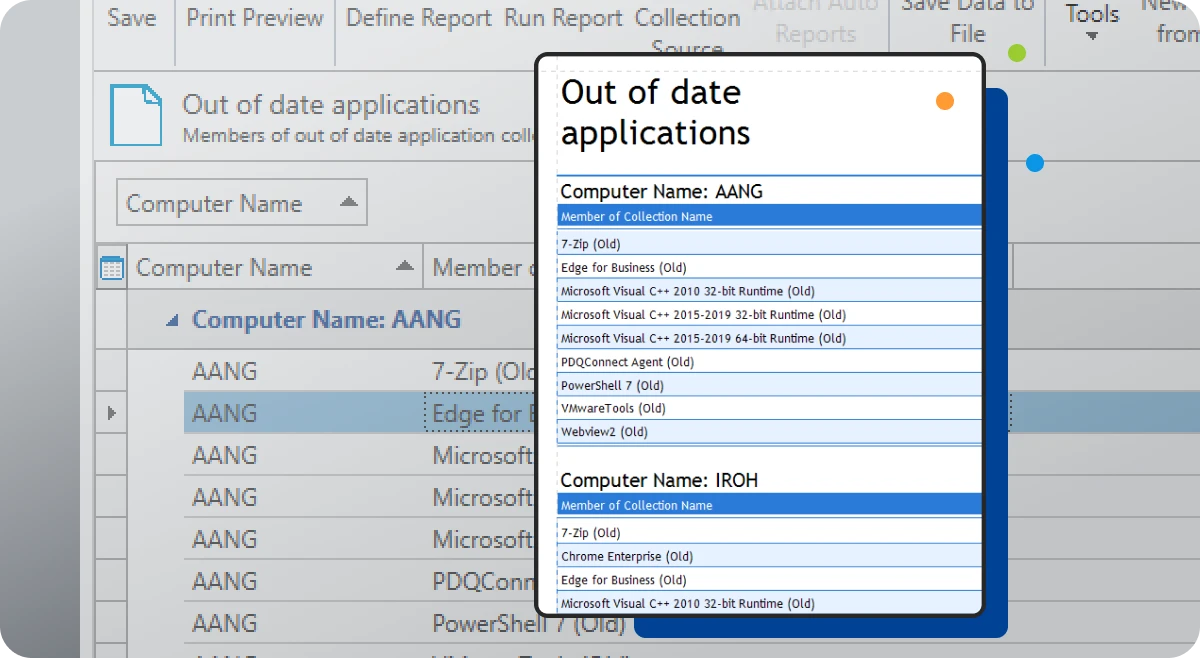

Targeted deployments
Automate your patch management by targeting PDQ Inventory collections for recurring deployments on a set schedule with PDQ Deploy.
Central server
Multiple admins at a single company can centrally maintain packages, deployment histories, and schedules across multiple administrators with high visibility.
Reporting
Gather insights and metrics with our prebuilt and custom reports. Schedule them to automatically run on a chosen cadence and email results to colleagues.
Trusted by thousands of companies, big and small
A perfect pairing
Use PDQ Deploy & Inventory together to manage on-prem or VPN-connected devices. One license gets you both!
Securely manage your Windows devices
PDQ Deploy & Inventory data is locally stored on your network, allowing you full control, offline operations, and more. We encrypt the password data we store for you as well as in-transit data.
Read more in our Product Security Guide.